The following is an article by Dr. Ali Abedi, a research lecturer at the Cheriton School of Computer Science. Dr. Abedi’s article appeared originally on APNIC Blog.
The APNIC blog article is based on a research study titled “WiFi Says “Hi!” Back to Strangers!” that Dr. Abedi conducted with Professor Omid Abari, which was presented at HotNets 2020, the 19th ACM Workshop on Hot Topics in Networks, held virtually from November 4–6, 2020.
In WiFi networks when a device sends a data packet, the receiving device sends an acknowledgement — or ACK — back to the transmitter. This mechanism is deployed to deal with error-prone wireless channels and to handle retransmissions in the physical and MAC layer. In particular, upon receiving a packet, the receiver calculates the cyclic redundancy check of the packet to detect possible errors. If the packet passes the check, the receiver sends an acknowledgment to the transmitter to notify the correct reception of the data packet.
Since most networks use security protocols such as WPA2 to prevent unauthorized devices from joining, one may assume that a WiFi device only acknowledges packets received from the associated access point or other devices in the same network.
Surprisingly, we have found that all of today’s WiFi devices acknowledge any packet they receive as long as the destination address matches their MAC address.

Dr. Ali Abedi is a lecturer at the Cheriton School of Computer Science. His research interests are primarily in battery-free wireless communication, Internet of Things, mmWave communication and performance evaluation.
The physical layer acknowledges all packets, even those without any valid payload, although higher layers eventually discard the fake packet.
Consider a scenario where a client device is connected to an access point, as shown in Figure 1. This is a private network secured by protocols such as WPA2. We found that if an attacker sends a fake and unencrypted 802.11 packet to the client device (labelled as victim), the client device sends back an acknowledgment.
We call this behaviour Polite WiFi because WiFi devices respond to any stranger with an acknowledgement.
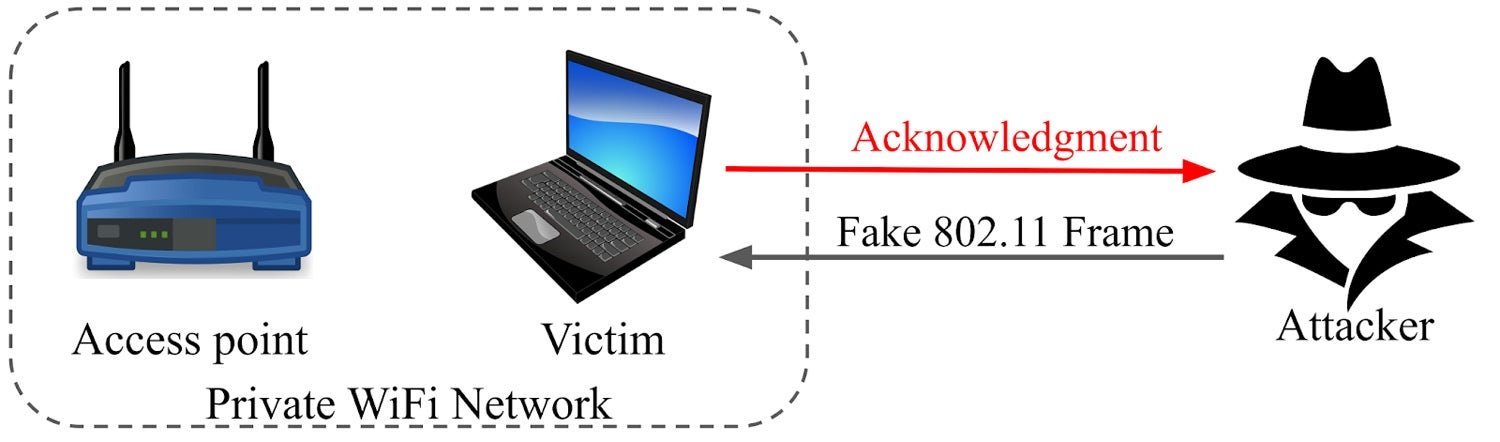
Figure 1. WiFi devices send an ACK for any packet they receive.
Testing the politeness of WiFi
We examined a few different WiFi devices in our lab and found that they were all vulnerable to Polite WiFi behaviour.
To extend this experiment to thousands of devices, we mounted a WiFi dongle on the roof of a vehicle and drove around the city to test all nearby devices. We used a Realtek RTL8812AU USB WiFi dongle connected to a Microsoft Surface, running Ubuntu 18.04. We developed a multi-threaded program using the Scapy library to discover nearby devices and sent fake 802.11 packets to the discovered devices, then verified that target devices responded to our fake packets.
We performed this experiment for one hour while driving around Waterloo, Ontario. In total, we discovered 5,328 WiFi nodes from 186 vendors, 1,523 different WiFi client devices from 147 vendors, and 3,805 access points from 94 vendors.
Table 1 shows the top 20 vendors for WiFi devices and WiFi access points in terms of number of devices discovered in our experiment. The list includes devices from major smartphone manufacturers, such as Apple, Google and Samsung, and major IoT vendors, such as Nest, Google, Amazon and Ecobee.
We found that all 5,328 WiFi Access Points and devices responded to our fake 802.11 packets with an acknowledgment. Therefore, we can assume most modern WiFi devices and access points are vulnerable to Polite WiFi.
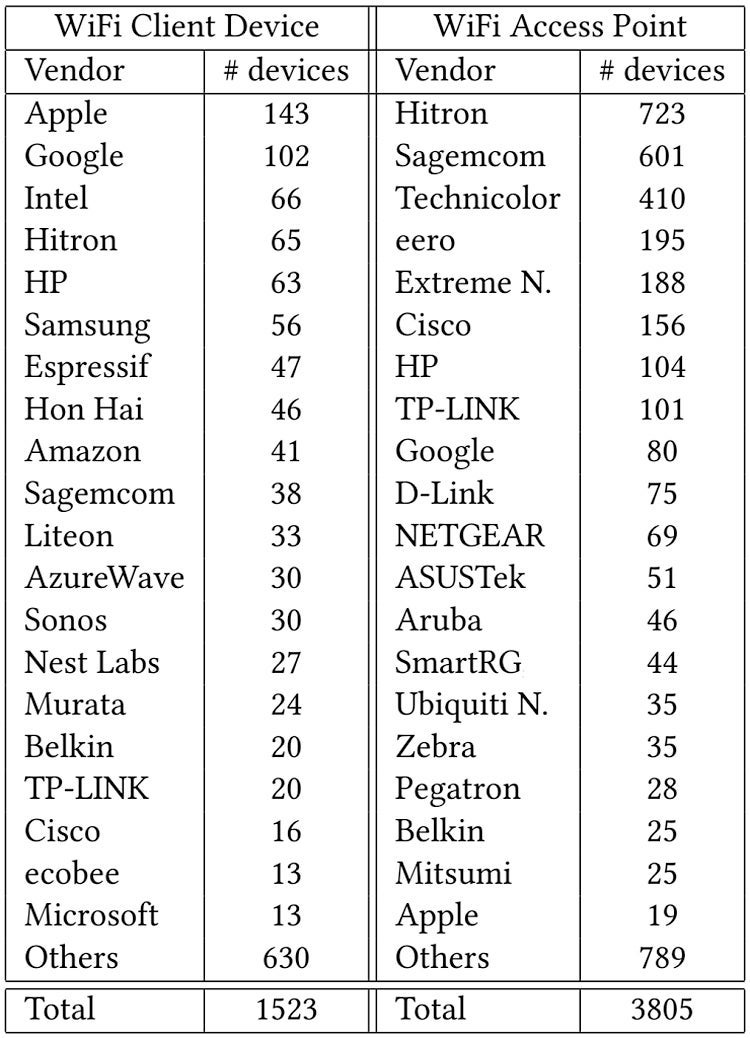
Table 1. List of WiFi devices and APs that responded to our fake 802.11 packets.
Potential threats from Polite WiFi
Polite WiFi behaviour creates many threats. For example, an attacker can send back-to-back fake packets to a victim device. Then, it can analyze the signal of the received ACKs to infer personal information about the victim.
Recent studies have shown that by monitoring WiFi signals one can infer some information about the environment such as localization, gesture recognition, breathing rate estimation, and keystroke inference. An attacker could exploit these systems and use the signal of ACKs to infer personal information.
To evaluate the feasibility of this attack, we conducted an experiment in which we tried to infer information from a target device — in this case, a Microsoft Surface Pro tablet. We placed an attacker device in a different room and implemented the attacking mechanism on an ESP32 WiFi module. The attacker had no access to the victim’s network nor did it have the secret key of this network. The attacker sent fake 802.11 packets to the target device, and measured the signal of received ACKs.
Figure 2 shows the amplitude of the signal received from the target device. When the tablet is on the ground, the signal amplitude is stable. However, as soon as a user approaches the device and picks it up the amplitude experiences large fluctuations.
Next, the user holds the tablet for about 10 seconds and then starts typing for about 10 seconds. It is clear that the pattern of just holding the tablet and typing are distinct.
This experiment shows that one can potentially reveal privacy-sensitive information by using Polite WiFi. An attacker can send fake packets to the devices inside a building to infer various information (about what is happening inside that building) by measuring changes in the signal of responses received.
We believe that many open questions require future study. Can an attacker detect occupancy? Can an attacker detect the activity of people inside a building? Or can an attacker estimate vital signs such as heart rate and breathing rate of people from the signal of their WiFi devices?
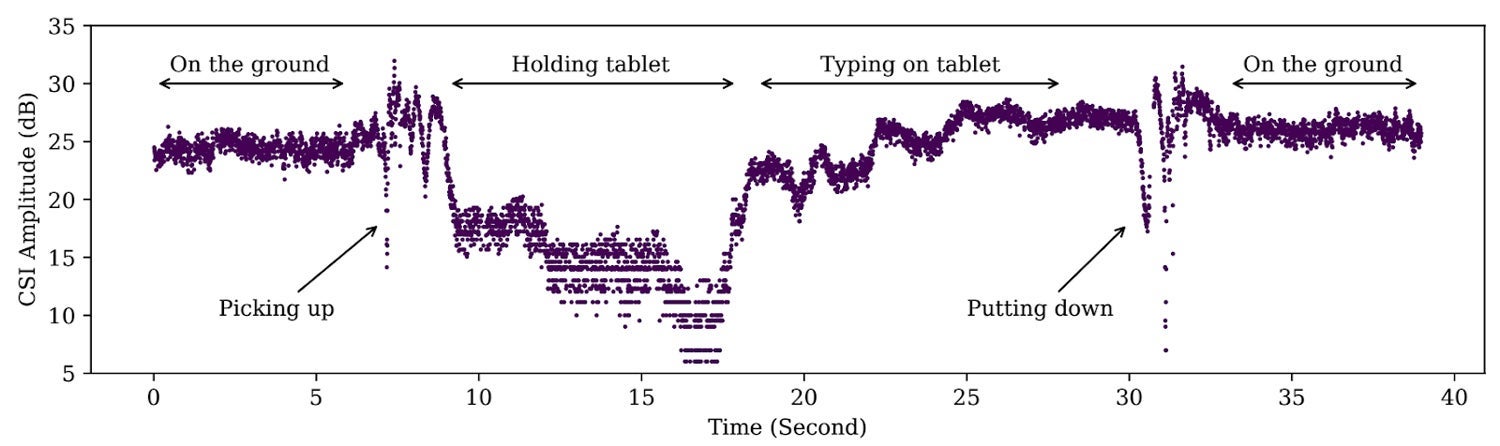
Figure 2. Variations of the received signal can potentially reveal privacy-sensitive information such as activities — possibly even the text typed on the device.