Certificate Updates
Here we describe the procedures for updating SSL certificates for web servers (https), IMAP servers (imaps), and other similar services (Dawn/Adrian - feel free to elaborate!)
Note Wed Oct 20 14:18:05 EDT 2021
Prior to today, the string "letsencrypt" did not occur in this twiki.
Since it's proper name Let's Encrypt is difficult to search for, using
the string as in their domain seems advisable.
In CSCF the direction has been to move all servers towards
Let's Encrypt
, but that does not
seem to have been documented in the twiki anywhere.
So, when contemplating a renewal, see if
Let's Encrypt
can be made to replace the installation in question.
Of course, letsencrypt is a specific means of utilizing
certbot and
certbot (NOT correctly rendered as the twikiwork
CertBot) is probably a better way to refer to the newer practice. On the otherhand, letsencrypt seems likely to remain the only client/provider for the certbot service. A more likely scenario is that other vendors produce analogous software.
Updating Hosts Certificates
Perhaps Try IST Documentation
Start at IST's documentation for SSL certificate management:
http://ist.uwaterloo.ca/security/IST-CA
(=>
https://ist.uwaterloo.ca/security/IST-CA/self-service/
)
(later became, ahem,
https://uwaterloo.ca/information-systems-technology/services/tlsssl-certificate-management/certificate-authority-details/globalsign-signed-x5093-certificates/self-service-globalsign-ssl-certificates
)
For Apache (1.3?) web servers the directive
SSLCACertificateFile /software/sslCerts-1/config/certs/cacert.pem needs to be present in the web server configuration, with that file containing the intermediate GlobalSign certificate.
See ST 67484 for an example that should be reworked into this wiki page.
--
DawnKeenan - 14 Apr 2010
Alternative "View" of this Page
An alternative version of this same information, with include files as links.
Useful command for examining and manipulating SSL certificates
Obtaining New or Renewed Certificates
Generate a New Private Key
Note that private keys must be kept as secret as possible.
Files containing private keys should preferably be readable only
by superuser (or perhaps
an equivalent service userid e.g.
www or
smmsp.
Generating a new key should be done in a private subdirectory;
the one containing the old key is an appropriate choice.
(But don't clobber the old key).
To generate a new private key, you can use the
openssl command.
Here we generate a 2048-bit key, placing it in file
new2048.key.
cscf.cs% openssl genrsa -out new2048.key 2048
Generating RSA private key, 2048 bit long modulus
........+++
.................................................................+++
e is 65537 (0x10001)
cscf.cs%
The
openssl command tends to be on a normal user path, and has
subcommands useful for examining and working with SSL certificates
and their components.
As of 2011,
GlobalSign Incorporated, the certificate authority chosen
by the University of Waterloo, requires a key (pair) of at least
2048 bits. Note the last argument on the command-line "2048".
You should use an appropriate
umask to ensure the privacy of
the private key, but it's probably
sufficient to
chmod afterwards. If it is necessary to transfer
a private key to another machine or user, be careful how you do it.
Note
In the past we would frequently re-use the old private key and use it to generate a new CSR when renewing a certificate. In fact, we began to assume that process, essentially generating a new expiry date for an existing public key, was what "renewing" meant. When GlobalSign required a change from 1024 to 2048 bit keys, that clearly could not be done. But furthermore, today (Wed May 11, 2011), http://www.globalsign.com/support/csrgen.php includes the statement includes the statement For higher server security GlobalSign does not allow reusing private keys. You must create a new key pair. That is, this process should almost certainly not be considered optional anymore. |
| In even more recent years, the above URL stopped returning such a definitive statement, and the requirement appears to have been removed. That might be because some products using SSL make it difficult to use a different private key. So whether this process is optional seems to depend on the software involved. It seems good practice to change the private key at each renewal, if possible. |
Generate a Certificate Signing Request (CSR)
| In the following I used cscf.cs.uwaterloo.ca as my sample hostname. This perhaps caused some confusion since the hostname was included in the email address we formerly used. |
The key part of renewing a certificate is generating a
Certificate Signing Request (
CSR) to send to the
Certificate Authority.
Generation of a Certificate Signing Request requires the ability
to read the private key, and so generally needs to be done as
superuser. (Though it's not technically necessary, as in my example
here).
The
openssl command can be used. Here we generate a request
for a certificate for host
cscf.cs.uwaterloo.ca.
- BLUE is text you type literally
- RED is text you must modify before typing
cscf.cs% openssl req -new -key ./new2048.key -out cscf.cs.uwaterloo.ca.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CA
State or Province Name (full name) [Some-State]:Ontario
Locality Name (eg, city) []:Waterloo
Organization Name (eg, company) [Internet Widgits Pty Ltd]:University of Waterloo
Organizational Unit Name (eg, section) []:
Common Name (eg, YOUR name) []:cscf.cs.uwaterloo.ca
Email Address []:username@domainname
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
cscf.cs% cat cscf.cs.uwaterloo.ca.csr
-----BEGIN CERTIFICATE REQUEST-----
MIIC6DCCAdACAQAwgaIxCzAJBgNVBAYTAkNBMRAwDgYDVQQIDAdPbnRhcmlvMREw
DwYDVQQHDAhXYXRlcmxvbzEfMB0GA1UECgwWVW5pdmVyc2l0eSBvZiBXYXRlcmxv
bzEdMBsGA1UEAwwUY3NjZi5jcy51d2F0ZXJsb28uY2ExLjAsBgkqhkiG9w0BCQEW
H2NzY2YtY2VydHNAY3NjZi5jcy51d2F0ZXJsb28uY2EwggEiMA0GCSqGSIb3DQEB
AQUAA4IBDwAwggEKAoIBAQC23vuprMTnHgMvwEDVbEVhEvjgFKkg4QqBxMhazy4f
b6x2xGmnxO/ef4LZPyF/RT0RUjTcQKAgLyafWGqYDopSr8Xunqy0G2EheqML2Eav
+Z8yGQ4vBjxXRaSj+1eiNX3VSYQOrM8d1A+mmbZYhyOVOmMkTrtQIhPriTv9j0Md
lBt0XVNn5bpt29cnSP4hz51Zh1xQmV32TTxyDE/pai1cSzmIXuv1oyzfiYhYeEJc
GaoSLNZKkv0oqdJkPbq7tlzGcWXdbHDJWPfY438lRF2bJWL3oojdRjZPQAMKanhy
Jpn04lvNjTCS1kofES1IDzHBHCzYH8d3GGLKU/XwqN87AgMBAAGgADANBgkqhkiG
9w0BAQUFAAOCAQEAAtkwipWtkH3ehVna3tWDseTknNg/MB8RZWp+mfrwvd3P30SS
uMNL15+z/Tso5+euxXFB/AUwuqgB4LnHPW9EPWjoxdaU4dWNKSNgJmIERMTgWFpw
COz8Byl39360nb7pdBWBgvyreizk8l4DsjJov+zi92SvyKHqjpf0p3zpYT6Ifp+A
ruzw9wX83v/DKfJPiNxXcV+aXEzBksCUEl3RGIGrxfvHf+5hPT2sdSb1KSh3kONl
UQ0KYyNAIvJO4O6Ia0OXaftXPit/VoS1j7mlpd4WdTXvqerq9wRn6ft/UAiiarkh
T1WLwniIE8TP/NJb351XsDgnCAvS93W6WXnx9Q==
-----END CERTIFICATE REQUEST-----
cscf.cs%
The
openssl command tends to be on a normal user path, and has
subcommands useful for examining and working with SSL certificates
and their components.
For example, you can use the
openssl command to give you a
more readable (well, detailed) version of the CSR.
cscf.cs% openssl req -text < cscf.cs.uwaterloo.ca.csr
Certificate Request:
Data:
Version: 0 (0x0)
Subject: C=CA, ST=Ontario, L=Waterloo, O=University of Waterloo, CN=cscf.cs.uwaterloo.ca/emailAddress=username@domainname
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (2048 bit)
Modulus (2048 bit):
00:b6:de:fb:a9:ac:c4:e7:1e:03:2f:c0:40:d5:6c:
45:61:12:f8:e0:14:a9:20:e1:0a:81:c4:c8:5a:cf:
2e:1f:6f:ac:76:c4:69:a7:c4:ef:de:7f:82:d9:3f:
21:7f:45:3d:11:52:34:dc:40:a0:20:2f:26:9f:58:
6a:98:0e:8a:52:af:c5:ee:9e:ac:b4:1b:61:21:7a:
a3:0b:d8:46:af:f9:9f:32:19:0e:2f:06:3c:57:45:
a4:a3:fb:57:a2:35:7d:d5:49:84:0e:ac:cf:1d:d4:
0f:a6:99:b6:58:87:23:95:3a:63:24:4e:bb:50:22:
13:eb:89:3b:fd:8f:43:1d:94:1b:74:5d:53:67:e5:
ba:6d:db:d7:27:48:fe:21:cf:9d:59:87:5c:50:99:
5d:f6:4d:3c:72:0c:4f:e9:6a:2d:5c:4b:39:88:5e:
eb:f5:a3:2c:df:89:88:58:78:42:5c:19:aa:12:2c:
d6:4a:92:fd:28:a9:d2:64:3d:ba:bb:b6:5c:c6:71:
65:dd:6c:70:c9:58:f7:d8:e3:7f:25:44:5d:9b:25:
62:f7:a2:88:dd:46:36:4f:40:03:0a:6a:78:72:26:
99:f4:e2:5b:cd:8d:30:92:d6:4a:1f:11:2d:48:0f:
31:c1:1c:2c:d8:1f:c7:77:18:62:ca:53:f5:f0:a8:
df:3b
Exponent: 65537 (0x10001)
Attributes:
a0:00
Signature Algorithm: sha1WithRSAEncryption
02:d9:30:8a:95:ad:90:7d:de:85:59:da:de:d5:83:b1:e4:e4:
9c:d8:3f:30:1f:11:65:6a:7e:99:fa:f0:bd:dd:cf:df:44:92:
b8:c3:4b:d7:9f:b3:fd:3b:28:e7:e7:ae:c5:71:41:fc:05:30:
ba:a8:01:e0:b9:c7:3d:6f:44:3d:68:e8:c5:d6:94:e1:d5:8d:
29:23:60:26:62:04:44:c4:e0:58:5a:70:08:ec:fc:07:29:77:
f7:7e:b4:9d:be:e9:74:15:81:82:fc:ab:7a:2c:e4:f2:5e:03:
b2:32:68:bf:ec:e2:f7:64:af:c8:a1:ea:8e:97:f4:a7:7c:e9:
61:3e:88:7e:9f:80:ae:ec:f0:f7:05:fc:de:ff:c3:29:f2:4f:
88:dc:57:71:5f:9a:5c:4c:c1:92:c0:94:12:5d:d1:18:81:ab:
c5:fb:c7:7f:ee:61:3d:3d:ac:75:26:f5:29:28:77:90:e3:65:
51:0d:0a:63:23:40:22:f2:4e:e0:ee:88:6b:43:97:69:fb:57:
3e:2b:7f:56:84:b5:8f:b9:a5:a5:de:16:75:35:ef:a9:ea:ea:
f7:04:67:e9:fb:7f:50:08:a2:6a:b9:21:4f:55:8b:c2:78:88:
13:c4:cf:fc:d2:5b:df:9d:57:b0:38:27:08:0b:d2:f7:75:ba:
59:79:f1:f5
-----BEGIN CERTIFICATE REQUEST-----
MIIC6DCCAdACAQAwgaIxCzAJBgNVBAYTAkNBMRAwDgYDVQQIDAdPbnRhcmlvMREw
DwYDVQQHDAhXYXRlcmxvbzEfMB0GA1UECgwWVW5pdmVyc2l0eSBvZiBXYXRlcmxv
bzEdMBsGA1UEAwwUY3NjZi5jcy51d2F0ZXJsb28uY2ExLjAsBgkqhkiG9w0BCQEW
H2NzY2YtY2VydHNAY3NjZi5jcy51d2F0ZXJsb28uY2EwggEiMA0GCSqGSIb3DQEB
AQUAA4IBDwAwggEKAoIBAQC23vuprMTnHgMvwEDVbEVhEvjgFKkg4QqBxMhazy4f
b6x2xGmnxO/ef4LZPyF/RT0RUjTcQKAgLyafWGqYDopSr8Xunqy0G2EheqML2Eav
+Z8yGQ4vBjxXRaSj+1eiNX3VSYQOrM8d1A+mmbZYhyOVOmMkTrtQIhPriTv9j0Md
lBt0XVNn5bpt29cnSP4hz51Zh1xQmV32TTxyDE/pai1cSzmIXuv1oyzfiYhYeEJc
GaoSLNZKkv0oqdJkPbq7tlzGcWXdbHDJWPfY438lRF2bJWL3oojdRjZPQAMKanhy
Jpn04lvNjTCS1kofES1IDzHBHCzYH8d3GGLKU/XwqN87AgMBAAGgADANBgkqhkiG
9w0BAQUFAAOCAQEAAtkwipWtkH3ehVna3tWDseTknNg/MB8RZWp+mfrwvd3P30SS
uMNL15+z/Tso5+euxXFB/AUwuqgB4LnHPW9EPWjoxdaU4dWNKSNgJmIERMTgWFpw
COz8Byl39360nb7pdBWBgvyreizk8l4DsjJov+zi92SvyKHqjpf0p3zpYT6Ifp+A
ruzw9wX83v/DKfJPiNxXcV+aXEzBksCUEl3RGIGrxfvHf+5hPT2sdSb1KSh3kONl
UQ0KYyNAIvJO4O6Ia0OXaftXPit/VoS1j7mlpd4WdTXvqerq9wRn6ft/UAiiarkh
T1WLwniIE8TP/NJb351XsDgnCAvS93W6WXnx9Q==
-----END CERTIFICATE REQUEST-----
I did the above just as an example. I generated a new key, and
will throw it and the CSR away without using them for anything
in production.
Notes
I have shown the inclusion of an email address. In fact,
GlobalSign does not include the email address in the certificates
they generate (that actually helps at renewal time) and so
really including that email address in the CSR is sort of
redundant. (When you submit the CSR in the next step, you
are required to enter an email address; that is presumably the
one
GlobalSign will actually use).
Furthermore, I have obfuscated the email address by representing
it symbolically. The address you should use now is
No permission to view CFPrivate.EMailAddressCscfCerts
If you want a certificate which can be used for several different names,
such as virtual hosts on a web server, you will want to see
Generate a CSR with Alternative Names.
Some Relevant History of https AltNames
This section needs more authorative references. And currently
makes a few dubious statements.
Perhaps this section is mostly apologetics(sic) for having developed
the practice of maintaining many Subject Alternative Names on
single https certificates.
The https protocol was changed a few years back so that a
single IP address could properly support multiple encryption
certificates.
Prior to that, a single IP address would necessarily need to use
one particular certificate (public key with additional information)
as the basis of the encryption.
To avoid needing a separate IP address for each desired named
server, the practice of using more than one (often many)
Subject Alternative Names was developed.
This is arguably becoming deprecated, at least for https.
(But note that also definitely deprecated is the past practice
of using the common name in the certicate as something
relevant to the connection; in general now, you
want to aim for a certificate with only a single Alternative Name,
or perhaps merely a few convenience aliases such as www.domain).
The work of determining which certificate to use should be done
in the browser virtual host set up. This will simplify
certificate maintenance (assuming certbot can be used), and
should also make the virtual hosts more independently
transportable to different physical servers.
Generate a Certificate Signing Request (CSR) Including Alt Names (SANs)
The method originally shown here was unreliable. It perhaps always was a red-herring, actually. It was based on the notion that using command-line options to specify certificate contents was a good idea. In fact, it would have always been better to learn how to edit and use an appropriate openssl.cnf type file. I will be learning to use such a .cnf file and hope to post details as a better alternative to this method. |
- BLUE is text you type literally
- RED is text you must modify before typing
But, in fact, in most cases in this page I use literal examples and assume
the reader can modify them for their own needs.
In 2015, it seemed that if you wanted to ask for additional
Subject Alternative Names (SANs) in your submission to
GlobalSign,
your CSR needed to contain matching information.
This method used here was taken directly from
http://blog.endpoint.com/2014/10/openssl-csr-with-alternative-names-one.html
Interesting enough, the blogger has replaced his method which I used here, creating a new version to show how to use a .cnf file instead. |
Observations regarding CSR and SANs
- SAN list in CSR must match old certificate exactly, including ordering
- SAN list entered in text box must match that, but minus the CN name
- That is, CSR and Certificate contain an extra SAN not in text box
- And you cannot change SANs as a side-effect while renewing
|
The
openssl command tends to be on a normal user path, and has
subcommands useful for examining and working with SSL certificates
and their components.
For example, you can use the
openssl command to give you a
more readable (well, detailed) version of the CSR.
root@www152# openssl req -text < test1.csr
Certificate Request:
Data:
Version: 0 (0x0)
Subject: C=CA, ST=Ontario, L=Waterloo, O=University of Waterloo, CN=cs.uwaterloo.ca/subjectAltName=DNS.1=www.cs.uwaterloo.ca,DNS.2=cs.uwaterloo.ca,DNS.3=www.scg.uwaterloo.ca,DNS.4=scg.uwaterloo.ca,DNS.5=odyssey.uwaterloo.ca,DNS.6=crysp.uwaterloo.ca,DNS.7=ripple.uwaterloo.ca,DNS.8=wwwtest.cs.uwaterloo.ca
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:d9:bb:01:33:73:fa:a5:03:e8:ee:51:eb:13:80:
80:ee:79:38:3e:8f:b5:35:0a:d3:f0:e8:19:f7:63:
6d:89:83:dd:0f:8e:6e:6a:d1:31:81:e9:76:71:cf:
d1:66:81:f3:1f:65:e6:eb:31:9f:86:e3:1d:99:75:
51:5f:e3:04:12:5a:57:bf:45:50:43:65:eb:85:3c:
a7:d7:b1:94:d6:42:ad:57:12:dd:8b:2b:f5:c8:c2:
bc:aa:3a:6a:4a:75:4c:70:dd:3d:09:f3:2f:96:97:
5e:62:e2:80:10:0e:0b:3b:30:2a:5a:86:1c:a3:7f:
b8:41:7f:bd:25:e6:2d:f7:1d:3c:16:1e:4d:b8:c3:
38:71:e1:8d:0f:3d:11:09:db:0e:6e:98:35:83:fe:
d2:b4:a2:76:e1:fb:71:51:e7:a0:11:57:15:3a:c1:
ad:9c:c1:d9:74:d2:f8:1f:66:1d:d3:10:da:dd:ba:
34:ab:90:b6:68:5a:b7:0e:4d:ee:84:1d:c1:1c:3f:
09:23:73:9d:3c:03:99:07:3e:8a:41:0b:2d:55:ad:
c7:22:24:9b:b0:08:8a:38:db:64:9f:5f:c0:f4:9d:
51:cc:a7:21:6e:c5:60:25:75:1c:28:25:b6:27:b4:
a6:81:e5:a0:ba:6e:df:c1:c8:78:0d:6a:2d:35:1e:
b7:71
Exponent: 65537 (0x10001)
Attributes:
a0:00
Signature Algorithm: sha1WithRSAEncryption
bf:0f:50:3f:aa:18:3a:04:62:5a:cd:3a:31:2b:94:38:ed:1e:
2d:29:c5:8e:d2:d3:30:d1:cb:5f:7a:91:ad:5c:4d:e3:40:17:
09:ff:26:91:0c:ef:41:ae:4d:d7:12:98:a9:35:79:82:c5:06:
1e:8d:18:63:45:2c:38:c5:aa:8d:1b:25:16:7a:3a:fd:87:6c:
bd:43:04:52:3b:ad:52:b7:7b:57:49:cd:72:ef:c1:94:86:e2:
84:73:10:ad:9a:d3:95:19:2a:78:f0:38:c5:0c:ae:d0:1b:c7:
cb:a7:0b:60:42:a2:f2:e5:a0:1c:35:8f:21:b8:9d:3e:a4:35:
92:62:8b:a8:c0:09:ef:46:2f:1a:66:0c:a6:9d:eb:39:17:42:
f2:35:82:82:5d:58:6f:ef:4c:79:20:57:2c:d2:5f:04:52:be:
f2:6c:c0:64:53:de:ad:ff:7b:a9:59:0a:f2:ad:50:5d:d8:54:
55:99:58:02:07:bf:79:01:15:3f:02:0b:ac:f9:3e:e3:03:cc:
d0:e0:79:00:df:65:63:08:bf:5a:39:0c:f6:84:42:8f:7f:66:
22:53:a3:ba:79:df:02:77:bc:a9:51:1a:e6:43:73:43:8a:01:
77:bd:fb:77:7a:47:da:c8:6f:35:1a:42:86:ad:94:99:7d:da:
04:d5:36:45
-----BEGIN CERTIFICATE REQUEST-----
MIIDjzCCAncCAQAwggFIMQswCQYDVQQGEwJDQTEQMA4GA1UECAwHT250YXJpbzER
MA8GA1UEBwwIV2F0ZXJsb28xHzAdBgNVBAoMFlVuaXZlcnNpdHkgb2YgV2F0ZXJs
b28xGDAWBgNVBAMMD2NzLnV3YXRlcmxvby5jYTGB2DCB1QYDVR0RDIHNRE5TLjE9
d3d3LmNzLnV3YXRlcmxvby5jYSxETlMuMj1jcy51d2F0ZXJsb28uY2EsRE5TLjM9
d3d3LnNjZy51d2F0ZXJsb28uY2EsRE5TLjQ9c2NnLnV3YXRlcmxvby5jYSxETlMu
NT1vZHlzc2V5LnV3YXRlcmxvby5jYSxETlMuNj1jcnlzcC51d2F0ZXJsb28uY2Es
RE5TLjc9cmlwcGxlLnV3YXRlcmxvby5jYSxETlMuOD13d3d0ZXN0LmNzLnV3YXRl
cmxvby5jYTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBANm7ATNz+qUD
6O5R6xOAgO55OD6PtTUK0/DoGfdjbYmD3Q+ObmrRMYHpdnHP0WaB8x9l5usxn4bj
HZl1UV/jBBJaV79FUENl64U8p9exlNZCrVcS3Ysr9cjCvKo6akp1THDdPQnzL5aX
XmLigBAOCzswKlqGHKN/uEF/vSXmLfcdPBYeTbjDOHHhjQ89EQnbDm6YNYP+0rSi
duH7cVHnoBFXFTrBrZzB2XTS+B9mHdMQ2t26NKuQtmhatw5N7oQdwRw/CSNznTwD
mQc+ikELLVWtxyIkm7AIijjbZJ9fwPSdUcynIW7FYCV1HCgltie0poHloLpu38HI
eA1qLTUet3ECAwEAAaAAMA0GCSqGSIb3DQEBBQUAA4IBAQC/D1A/qhg6BGJazTox
K5Q47R4tKcWO0tMw0ctfepGtXE3jQBcJ/yaRDO9Brk3XEpipNXmCxQYejRhjRSw4
xaqNGyUWejr9h2y9QwRSO61St3tXSc1y78GUhuKEcxCtmtOVGSp48DjFDK7QG8fL
pwtgQqLy5aAcNY8huJ0+pDWSYouowAnvRi8aZgymnes5F0LyNYKCXVhv70x5IFcs
0l8EUr7ybMBkU96t/3upWQryrVBd2FRVmVgCB795ARU/Agus+T7jA8zQ4HkA32Vj
CL9aOQz2hEKPf2YiU6O6ed8Cd7ypURrmQ3NDigF3vft3ekfayG81GkKGrZSZfdoE
1TZF
-----END CERTIFICATE REQUEST-----
I did the above just as an example. I generated a new key, and
will throw it and the CSR away without using them for anything
in production.
Notes
The final generated certificate must include the name specified
in the
CN field in the
Subject Alternative Name section.
For this reason, we arrange to specify it in our CSR, and that
seems to work.
An oddity is, however, that in the corresponding box where
GlobalSign
requires you list the SAN values, you must omit that value. (Although
GlobalSign always includes the
CN value in the SAN list).
In the submission stage (which will mostly be covered later),
at the
GlobalSign submission page, you must select
Add specific Subject Alternative Names (SANs)
[ ] No [X] Yes
That expands and opens up four more options
- Activate Standard Unified Communications (UC) Support
- Secure Additional Subdomains
- Secure Public IP Addresses
- Secure Additional Domain Names
You actually want to select, expand, and proceed with
Secure Additional Subdomains.
The option is badly titled and likely should say
Fully Qualified Domain Names
instead of subdomains.
In particular, you will get nowhere if you try
Secure Additional Domain Names
since in that case, all names must be non-FQDN, and, I think,
relative to the CN of the certificate.
Actual Certificate Generated by a Very Similar Request
The following production certificate was generated (i.e. received from
GlobalSign after appropriately submitting the CSR at their form page)
using a CSR very similar to the above, but with a different
private/public key pair.
Note where the specified names appear in the
Subject Alternative Name
section in the
X509v3 extensions section.
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
11:21:90:7a:78:1d:e5:b4:7e:fd:18:b8:b3:48:47:59:2c:f7
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=BE, O=GlobalSign nv-sa, CN=GlobalSign Organization Validation CA - SHA256 - G2
Validity
Not Before: Mar 25 17:51:09 2015 GMT
Not After : Mar 25 17:51:09 2016 GMT
Subject: C=CA, ST=Ontario, L=Waterloo, O=University of Waterloo, CN=cs.uwaterloo.ca
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:d9:bb:ed:a7:25:6a:e6:d3:9a:59:95:af:88:2e:
8b:24:2a:97:20:41:51:80:b3:d5:35:6a:6e:a7:0c:
90:dd:3b:ca:ca:d6:4e:9a:2b:69:b0:ee:fa:79:dd:
4e:80:18:08:ef:43:e2:a2:06:07:a8:43:75:10:7e:
f4:ac:d2:70:44:7f:94:11:b4:0a:0b:1b:9a:a9:41:
9b:8b:35:82:da:44:cf:b2:44:54:3a:31:be:80:6c:
79:53:d7:51:9c:4f:e8:75:bd:51:ae:3a:45:4e:d2:
f9:3a:1c:03:c7:d4:9e:c2:ee:3b:8f:9a:80:08:1a:
fc:67:a9:f1:cc:ae:ae:93:8b:52:c4:3e:cf:58:c2:
14:3a:4a:4c:4f:df:86:e3:0c:11:6d:70:22:be:2f:
6b:43:5a:e3:4c:fe:5c:42:52:9c:b0:68:6a:9e:6a:
a2:66:e8:a1:0c:69:0e:94:84:3f:42:ec:53:a7:fa:
d3:1a:eb:b6:f8:ef:eb:cb:97:8e:c4:0d:1d:86:13:
ae:59:2b:a1:d4:8a:27:a9:9b:3a:b1:f8:1e:cc:06:
6b:a7:fe:8a:41:be:12:d2:af:0e:93:5c:97:1d:c7:
8f:f2:e4:0c:aa:3d:e4:f9:3e:bc:04:72:44:df:50:
e3:d8:74:0f:96:93:c9:05:53:fe:14:df:05:8e:0c:
99:07
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Certificate Policies:
Policy: 2.23.140.1.2.2
CPS: https://www.globalsign.com/repository/
X509v3 Subject Alternative Name:
DNS:cs.uwaterloo.ca, DNS:www.cs.uwaterloo.ca, DNS:www.scg.uwaterloo.ca, DNS:scg.uwaterloo.ca, DNS:odyssey.uwaterloo.ca, DNS:crysp.uwaterloo.ca, DNS:ripple.uwaterloo.ca, DNS:wwwtest.cs.uwaterloo.ca
X509v3 Basic Constraints:
CA:FALSE
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 CRL Distribution Points:
Full Name:
URI:http://crl.globalsign.com/gs/gsorganizationvalsha2g2.crl
Authority Information Access:
CA Issuers - URI:http://secure.globalsign.com/cacert/gsorganizationvalsha2g2r1.crt
OCSP - URI:http://ocsp2.globalsign.com/gsorganizationvalsha2g2
X509v3 Subject Key Identifier:
42:EF:03:65:9D:95:7A:02:67:30:B5:DB:2B:FB:CB:A3:69:2A:9E:1C
X509v3 Authority Key Identifier:
keyid:96:DE:61:F1:BD:1C:16:29:53:1C:C0:CC:7D:3B:83:00:40:E6:1A:7C
Signature Algorithm: sha256WithRSAEncryption
5b:84:5c:ba:46:e7:1e:95:34:1c:8a:92:dd:4a:6c:ef:82:2f:
12:b1:91:05:aa:c4:30:f8:83:75:c4:3e:06:3c:11:4d:0b:14:
7c:a4:d3:ca:e7:a9:e3:93:f3:76:5a:15:1d:81:f4:e4:cf:8d:
0d:1a:93:34:74:7d:15:29:aa:29:26:2e:c4:ea:33:ce:09:9c:
0f:17:f7:2f:ed:92:21:a1:9c:6a:ef:4e:1d:64:7c:51:e5:0a:
bf:1f:41:e9:20:a1:6d:ad:d6:5b:9b:e3:01:95:52:58:8f:b3:
9f:d3:5f:8d:93:bb:ef:ae:37:b1:81:b4:d2:1b:76:2b:1d:4c:
f8:9e:af:ea:2b:21:7a:90:9d:f5:57:5e:e6:4d:0e:44:6c:ae:
39:d3:b0:60:73:82:fa:d9:3d:c9:8a:24:5a:de:d2:6f:33:0a:
5d:51:64:75:f6:24:16:e6:81:1e:2b:da:2a:b8:c7:14:cc:3d:
5d:ee:ec:b4:f4:7c:20:a8:e0:95:05:36:b9:b5:05:e1:c3:26:
08:1e:14:84:19:8f:fa:94:97:2c:78:53:84:64:11:6b:0c:b3:
89:d3:f2:46:ca:3e:f4:2c:61:2d:dd:64:f7:f5:0e:60:cd:79:
8a:38:43:d3:c1:61:26:64:f7:14:59:6f:a2:fb:be:3e:d4:87:
3f:31:8b:8d
-----BEGIN CERTIFICATE-----
MIIFzDCCBLSgAwIBAgISESGQengd5bR+/Ri4s0hHWSz3MA0GCSqGSIb3DQEBCwUA
MGYxCzAJBgNVBAYTAkJFMRkwFwYDVQQKExBHbG9iYWxTaWduIG52LXNhMTwwOgYD
VQQDEzNHbG9iYWxTaWduIE9yZ2FuaXphdGlvbiBWYWxpZGF0aW9uIENBIC0gU0hB
MjU2IC0gRzIwHhcNMTUwMzI1MTc1MTA5WhcNMTYwMzI1MTc1MTA5WjBtMQswCQYD
VQQGEwJDQTEQMA4GA1UECBMHT250YXJpbzERMA8GA1UEBxMIV2F0ZXJsb28xHzAd
BgNVBAoTFlVuaXZlcnNpdHkgb2YgV2F0ZXJsb28xGDAWBgNVBAMTD2NzLnV3YXRl
cmxvby5jYTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBANm77aclaubT
mlmVr4guiyQqlyBBUYCz1TVqbqcMkN07ysrWTporabDu+nndToAYCO9D4qIGB6hD
dRB+9KzScER/lBG0CgsbmqlBm4s1gtpEz7JEVDoxvoBseVPXUZxP6HW9Ua46RU7S
+TocA8fUnsLuO4+agAga/Gep8cyurpOLUsQ+z1jCFDpKTE/fhuMMEW1wIr4va0Na
40z+XEJSnLBoap5qombooQxpDpSEP0LsU6f60xrrtvjv68uXjsQNHYYTrlkrodSK
J6mbOrH4HswGa6f+ikG+EtKvDpNclx3Hj/LkDKo95Pk+vARyRN9Q49h0D5aTyQVT
/hTfBY4MmQcCAwEAAaOCAmswggJnMA4GA1UdDwEB/wQEAwIFoDBJBgNVHSAEQjBA
MD4GBmeBDAECAjA0MDIGCCsGAQUFBwIBFiZodHRwczovL3d3dy5nbG9iYWxzaWdu
LmNvbS9yZXBvc2l0b3J5LzCBsQYDVR0RBIGpMIGmgg9jcy51d2F0ZXJsb28uY2GC
E3d3dy5jcy51d2F0ZXJsb28uY2GCFHd3dy5zY2cudXdhdGVybG9vLmNhghBzY2cu
dXdhdGVybG9vLmNhghRvZHlzc2V5LnV3YXRlcmxvby5jYYISY3J5c3AudXdhdGVy
bG9vLmNhghNyaXBwbGUudXdhdGVybG9vLmNhghd3d3d0ZXN0LmNzLnV3YXRlcmxv
by5jYTAJBgNVHRMEAjAAMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjBJ
BgNVHR8EQjBAMD6gPKA6hjhodHRwOi8vY3JsLmdsb2JhbHNpZ24uY29tL2dzL2dz
b3JnYW5pemF0aW9udmFsc2hhMmcyLmNybDCBoAYIKwYBBQUHAQEEgZMwgZAwTQYI
KwYBBQUHMAKGQWh0dHA6Ly9zZWN1cmUuZ2xvYmFsc2lnbi5jb20vY2FjZXJ0L2dz
b3JnYW5pemF0aW9udmFsc2hhMmcycjEuY3J0MD8GCCsGAQUFBzABhjNodHRwOi8v
b2NzcDIuZ2xvYmFsc2lnbi5jb20vZ3Nvcmdhbml6YXRpb252YWxzaGEyZzIwHQYD
VR0OBBYEFELvA2WdlXoCZzC12yv7y6NpKp4cMB8GA1UdIwQYMBaAFJbeYfG9HBYp
UxzAzH07gwBA5hp8MA0GCSqGSIb3DQEBCwUAA4IBAQBbhFy6RucelTQcipLdSmzv
gi8SsZEFqsQw+IN1xD4GPBFNCxR8pNPK56njk/N2WhUdgfTkz40NGpM0dH0VKaop
Ji7E6jPOCZwPF/cv7ZIhoZxq704dZHxR5Qq/H0HpIKFtrdZbm+MBlVJYj7Of01+N
k7vvrjexgbTSG3YrHUz4nq/qKyF6kJ31V17mTQ5EbK4507Bgc4L62T3JiiRa3tJv
MwpdUWR19iQW5oEeK9oquMcUzD1d7uy09HwgqOCVBTa5tQXhwyYIHhSEGY/6lJcs
eFOEZBFrDLOJ0/JGyj70LGEt3WT39Q5gzXmKOEPTwWEmZPcUWW+i+74+1Ic/MYuN
-----END CERTIFICATE-----
If This Does Not Seem to Work
If, even after diddling the
GlobalSign submission page to specify
the SANs in an appropriate box, your submission still fails with
something like "SANs do not match certificate request", then you
might need to resort to the more complicated procedure, currently
documented at
*
http://apetec.com/support/GenerateSAN-CSR.htm Need note or new Include page here about OrganizationSSL versus IntranetSSL,
Need note or new Include page here about OrganizationSSL versus IntranetSSL,
Submit the CSR to the Certificate Authority
To obtain an actual certificate, you must submit the
CSR
to the
Certificate Authority
(
GlobalSign,
http://www.globalsign.com/
).
To get to the right web page, you need a particular URL which
encodes a login session. I will not reproduce that here. Obtain
it directly from e.g. someone in IST.
(Hint: the URL looks like
https://system.globalsign.com/direct_en/directpv.do?domain=MAGIC
where "MAGIC" is the special part which identifies you as University of Waterloo).
Here is a screenshot showing such a successful session, thereby indicating the top options and settings for a Certificate Request; note
OrganizationSSL versus
IntranetSSL choice:
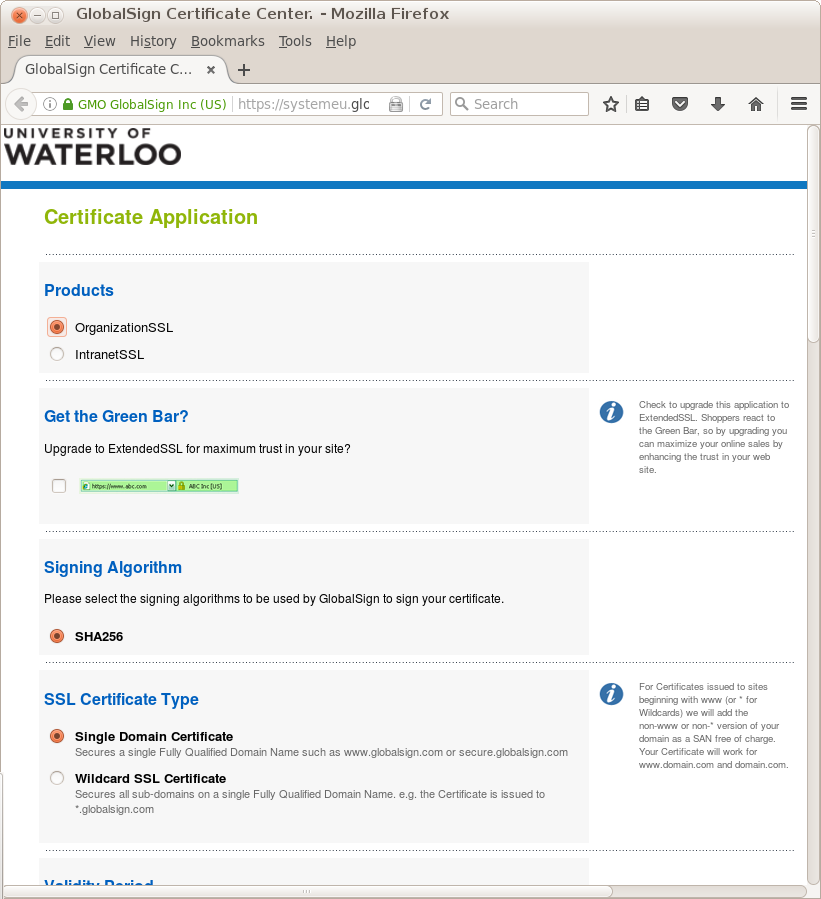
There is an option you must select to choose new certificate or
renewal.
If
GlobalSign had never signed a certificate for the particular
host before, then you must choose the option for a new certificate.
Otherwise, you can possibly choose "renewal".
Note that, in the case of a renewal,
the private key used for the CSR does not need to match
the public key in the old certificate.
That is, often when doing renewals you will keep the old private
key (this has later implications which ease installation), but
in fact the private key can be changed at renewal time. (As was
actually necessary when
GlobalSign began in 2011 requiring a
minimum key
size of 2048 bits.
The following is a sample of a CSR which looks like what you need
to cut-and-paste into the web page form. (but don't actually use this
sample!)
-----BEGIN CERTIFICATE REQUEST-----
MIIC6DCCAdACAQAwgaIxCzAJBgNVBAYTAkNBMRAwDgYDVQQIDAdPbnRhcmlvMREw
DwYDVQQHDAhXYXRlcmxvbzEfMB0GA1UECgwWVW5pdmVyc2l0eSBvZiBXYXRlcmxv
bzEdMBsGA1UEAwwUY3NjZi5jcy51d2F0ZXJsb28uY2ExLjAsBgkqhkiG9w0BCQEW
H2NzY2YtY2VydHNAY3NjZi5jcy51d2F0ZXJsb28uY2EwggEiMA0GCSqGSIb3DQEB
AQUAA4IBDwAwggEKAoIBAQC23vuprMTnHgMvwEDVbEVhEvjgFKkg4QqBxMhazy4f
b6x2xGmnxO/ef4LZPyF/RT0RUjTcQKAgLyafWGqYDopSr8Xunqy0G2EheqML2Eav
+Z8yGQ4vBjxXRaSj+1eiNX3VSYQOrM8d1A+mmbZYhyOVOmMkTrtQIhPriTv9j0Md
lBt0XVNn5bpt29cnSP4hz51Zh1xQmV32TTxyDE/pai1cSzmIXuv1oyzfiYhYeEJc
GaoSLNZKkv0oqdJkPbq7tlzGcWXdbHDJWPfY438lRF2bJWL3oojdRjZPQAMKanhy
Jpn04lvNjTCS1kofES1IDzHBHCzYH8d3GGLKU/XwqN87AgMBAAGgADANBgkqhkiG
9w0BAQUFAAOCAQEAAtkwipWtkH3ehVna3tWDseTknNg/MB8RZWp+mfrwvd3P30SS
uMNL15+z/Tso5+euxXFB/AUwuqgB4LnHPW9EPWjoxdaU4dWNKSNgJmIERMTgWFpw
COz8Byl39360nb7pdBWBgvyreizk8l4DsjJov+zi92SvyKHqjpf0p3zpYT6Ifp+A
ruzw9wX83v/DKfJPiNxXcV+aXEzBksCUEl3RGIGrxfvHf+5hPT2sdSb1KSh3kONl
UQ0KYyNAIvJO4O6Ia0OXaftXPit/VoS1j7mlpd4WdTXvqerq9wRn6ft/UAiiarkh
T1WLwniIE8TP/NJb351XsDgnCAvS93W6WXnx9Q==
-----END CERTIFICATE REQUEST-----
And here follows an example of an old certificate which looks like what you
need to cut-and-paste into the web page form. (but don't actually use this
sample!)
-----BEGIN CERTIFICATE-----
MIIE+jCCA+KgAwIBAgILAQAAAAABKRmXjogwDQYJKoZIhvcNAQEFBQAwajEjMCEG
A1UECxMaT3JnYW5pemF0aW9uIFZhbGlkYXRpb24gQ0ExEzARBgNVBAoTCkdsb2Jh
bFNpZ24xLjAsBgNVBAMTJUdsb2JhbFNpZ24gT3JnYW5pemF0aW9uIFZhbGlkYXRp
b24gQ0EwHhcNMTAwNjA4MjEwNjA5WhcNMTEwODE2MTM0ODA5WjByMQswCQYDVQQG
EwJDQTEQMA4GA1UECBMHT250YXJpbzERMA8GA1UEBxMIV2F0ZXJsb28xHzAdBgNV
BAoTFlVuaXZlcnNpdHkgb2YgV2F0ZXJsb28xHTAbBgNVBAMMFGNzY2YuY3MudXdh
dGVybG9vLmNhMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAu9DAZcrz
KtWx7GNsbKig6LqFtU1PDmL1S5JfhMz23J2ISLfMXHIrW+8H5rrT5UzC59u8eZO5
YdO5dSllRtoOXYWfLaCz2+axONOQrN08av7S6+0uyYD8ioF6ZgoW2J4Xn0T/ruVQ
we9fHavje6TkYE00qat1e+72YGX95FmiX3juzTrJ0HUKTCsMDS2JuvOU3z4xcyyH
yO1vLZfmtRtkS13aOBWsb/Tf6WTjfxPR3FdMBauLSVEYEXUKBpuDMbOagN4CoBTq
AbEfZo4rLcufaPFL2Sxcr+yVKOXpoTwG83YSpwM/NWf4+Y9CQ+2qfYQtWP8Xm3vg
fZhGEUu6UCWWFwIDAQABo4IBlzCCAZMwHwYDVR0jBBgwFoAUfW0q7Garp1E2qwJp
8XCPxFkLmh8wSQYIKwYBBQUHAQEEPTA7MDkGCCsGAQUFBzAChi1odHRwOi8vc2Vj
dXJlLmdsb2JhbHNpZ24ubmV0L2NhY2VydC9vcmd2MS5jcnQwPwYDVR0fBDgwNjA0
oDKgMIYuaHR0cDovL2NybC5nbG9iYWxzaWduLm5ldC9Pcmdhbml6YXRpb25WYWwx
LmNybDAdBgNVHQ4EFgQUfHNlksoZYTqu2nJYNBJK2APW+F4wCQYDVR0TBAIwADAO
BgNVHQ8BAf8EBAMCBaAwKQYDVR0lBCIwIAYIKwYBBQUHAwEGCCsGAQUFBwMCBgor
BgEEAYI3CgMDMEsGA1UdIAREMEIwQAYJKwYBBAGgMgEUMDMwMQYIKwYBBQUHAgEW
JWh0dHA6Ly93d3cuZ2xvYmFsc2lnbi5uZXQvcmVwb3NpdG9yeS8wEQYJYIZIAYb4
QgEBBAQDAgbAMB8GA1UdEQQYMBaCFGNzY2YuY3MudXdhdGVybG9vLmNhMA0GCSqG
SIb3DQEBBQUAA4IBAQBkFzKLz37xdXPbbspX4ST3NVd4a4ThH+qoDu2l1/7TsZ8J
RDeDxQf4ckmPSYya9nJRNDAfF47o1P6hmfiw20CbPefKwHc5Tf+xdy1QTa0ivJtJ
grmC2Cc74b6pe51MawEDD0N8qFjJjQENXlQ5MXoqbPsKER6I9H7pbZHvfqJG0UXE
iQmieXQu0p+FxsKNOn+dyO9j6NKSL8l3Rr4H+tqLQK+fHvSeQKo1q11Q8soUM7Ql
/3tVT/qLTzEy8QRkYRF9p+3ihQEIhyYFDD9JnSiLeOsQvxhAj+jEqdS+w15p3ORR
/xbBgIXEOKKniB9CLXLKQuOTXMl2HxTWMSCubBAu
-----END CERTIFICATE-----
In addition to the CSR (and optionally old Certificate), the form
requires 4 pieces of information,
- First Name
- Last Name
- Telephone (inc. region code)
- Email Address
For First and Last Name, enter your own (something IST will recognize).
For Email Address, CS should always use
No permission to view CFPrivate.EMailAddressCscfCerts
For the telephone number, I always use
+1 519 888 4567 (in that format).
You must first click "Continue" to submit the page, then an "I Agree" to
an Agreement (suffixed to confirmation of details).
After the
CSR has been so submitted to the
Certificate Authority
(
http://www.globalsign.com/
) they will contact
University of Waterloo IST to verify the request (and arrange for
payment).
Once the
CSR has been submitted, it is of no further use and can
be deleted.
Receive the Certificate from the Certificate Authority
You should receive almost immediately an almost useless email
message analogous to the following.
From gasemails-us@globalsign.com Fri Jan 28 17:41:15 2011
Message-ID: <2059314663.1296254454773.JavaMail.gsadmin@gsgas04.globalsign.com>
Date: Sat, 29 Jan 2011 07:40:54 +0900 (JST)
From: gasemails-us@globalsign.com
To: redacted@redacted.uwaterloo.ca
Subject: CE201102140123: Order Received for cscf.cs.uwaterloo.ca
== GlobalSign / Certificate application received ================
======================================================================
Please note this e-mail is automatically generated. If you need
assistance please refer to the "Contact Us" information below.
======================================================================
Thank you for your SSL Managed Service order.
Please make sure to review the following application details.
For the further application details, please confirm them
on GlobalSign Certificate Center.
***Your Order Information
--------------------------------------------------
[Order Number] CE201102140123
[Common Name] cscf.cs.uwaterloo.ca
[Product] OrganizationSSL(MSSL)
[Period] 1 years
[Number of Licenses] 1
--------------------------------------------------
***Your Certificate Information
Common Name cscf.cs.uwaterloo.ca
Organization
City or Locality
State or Province
Country
--------------------------------------------------
***Your Billing Information
[Billing Contact]
[Payment Method] Bulk/deposit
[Special Instruction]
[Total Amount] usd 88.00(include tax)
***Prevetted Domains -
--------------------------------------------------
***Ordering Process
--------------------------------------------------
When ordering SSL Managed Service it is possible that you will
need to submit corporate documents.
Please see details on the below URL:
http://www.globalsign.com/support/ssl-order/pv-organization-ssl.html
The period for which prevetting remains valid is one year.
***GAS Login for Management of Certificate(s)
--------------------------------------------------
Login to the GlobalSign Certificate Center to manage the lifecycle
of your certificate. The GlobalSign Certificate Center gives you easy
access to renew certificates and how to revoke or cancel should it
be necessary.
https://systemeu.globalsign.com/loginpartner_en/loginpartner.do
GlobalSign will refund your certificate in full if you cancel
within 7 days of the issuance of the certificate.
***GlobalSign Certificate Center Login for Billing Management
--------------------------------------------------
Login to the GlobalSign Certificate Center to view billing details,
request additional receipts and process any outstanding invoices.
http://www.globalsign.com/support/gas/invoice.html
***Renewing your Certificate
--------------------------------------------------
To assist you in making sure that your certificate does not expire
GlobalSign will send you email reminders beginning 90 days before
expiration. If you renew early you will receive discounted pricing
and other fantastic loyalty benefits.
***Agreements
--------------------------------------------------
Please confirm the GlobalSign CPS and Agreements below:
http://www.globalsign.com/repository
***Contact Us
--------------------------------------------------
For Technical Support & Account Queries:
http://www.globalsign.com/support
http://www.globalsign.com/help.html
Tel: Use below numbers
GlobalSign Contact Details:
Support: 877-467-7543 (toll free)
Sales: 877-775-4562 (toll free)
Fax: 603-570-7059
Please fax documents for vetting directly to 617-830-0779.
--------------------------------------------------------------------------------------
GlobalSign - A Leader in Online Security & Authentication Solutions for over 10 years.
--------------------------------------------------------------------------------------
And then, assuming University of Waterloo IST approves the request,
you will receive, within a day or so, email similar to the following,
which actually contains the certificate you need.
From gasemails-us@globalsign.com Fri Jan 28 18:58:35 2011
Message-ID: <4784274.1296259086559.JavaMail.gsadmin@gsbatch01.globalsign.com>
Date: Sat, 29 Jan 2011 08:58:06 +0900 (JST)
From: gasemails-us@globalsign.com
To: redacted@redacted.uwaterloo.ca
Subject: CE201101296349: Your SSL Certificate for plg1.cs.uwaterloo.ca has been issued.
Congratulations! Your GlobalSign SSL Certificate has now been issued.
[Order Number] CE201101296349
[Common Name] plg1.cs.uwaterloo.ca
***YOUR OrganizationSSL CERTIFICATE
----------------------------------------------------
Your SSL and Intermediate Certificates can be found at the bottom of this email.
Alternatively, you may log into your GlobalSign Certificate Center (GCC) account and Copy and Paste your SSL Certificate file from there.
GlobalSign Certificate Center:
http://www.globalsign.com/support/gas/get-certificate.html
***INSTALLING YOUR CERTIFICATEs:
----------------------------------------------------
You can also find your Intermediate Certificate, detailed tutorials, guides and manuals on installing your Certificates using the link below to access the Support Area:
Support Area:
http://www.globalsign.com/support/index.html
***QUICK INSTALLATION GUIDE:
----------------------------------------------------
1) Using a text editor, copy the Intermediate Certificate text from the bottom of this email, (including the -----BEGIN CERTIFICATE----- and -----END CERTIFICATE----- lines) and save it to a file such as gs_intermediate_domain_ca.txt
2) Using a text editor, copy the SSL Certificate text, from the bottom of this email (including the -----BEGIN CERTIFICATE----- and -----END CERTIFICATE----- lines) and save it to a file such as yourdomain.txt
3) Copy these .txt files to your server, and then rename them with .crt extensions.
4) Install the Intermediate and SSL Certificates
5) Restart your server
6)Test on any non-IE browser to ensure correct installation of both Certificates
7) Install your Site Seal
8) We suggest you back-up your SSL Certificate and Private Key pair and keep it safe, all IIS users can use the Export Wizard
***INSTALLING YOUR FREE SITE SEAL:
----------------------------------------------------
The GlobalSign Site seal is a sign of trust on the Internet. It shows your customers you have been authenticated and you use the strongest SSL possible to secure your transactions. Displaying the GlobalSign Site Seal will help visitors trust your web site, and then help convert general visitors to paying customers. Don't risk people abandoning shopping carts and web forms - display the GlobalSign site seal to give them the confidence to complete the transaction.
Installing the GlobalSign Site Seal is easy - just follow the link below:
http://www.globalsign.com/support/ssl-site-seal.html
----------------------------------------------------
RETAIL CUSTOMERS Upgrade to SSL Managed Service If you are using multiple SSL Certificates for your organization, speak to Sales about saving costs by upgrading to the SSL Managed Service. This upgrade is automatic and gives you immediate discounts, granular user management and allows you to submit your domains for pre-vetting. When you need a new SSL Certificate you simply log in and apply, your SSL Certificate will be issued instantly.
SSL RESELLER PARTNER OPPORTUNITIES
Is your organization buying SSL on behalf of your customers? Talk to us today about reselling GlobalSign SSL Certificates. Use GAS to manage end customer SSL requirements as well as your own SSL Resellers and gain discounts on Pay As You Go.
We hope that your application process was quick and easy and you have
enjoyed the GlobalSign experience.
***CONTACT US
--------------------------------------------------
For Technical Support & Account Queries:
http://www.globalsign.com/support
http://www.globalsign.com/help.html
Global Office Contact Details:
Toll Free: 877-775-4562 | Fax: +1 603-570-7059
--------------------------------------------------
A Leader in Online Security & Authentication Solutions for over
10 years
--------------------------------------------------
Your SSL Certificate (Formatted for the majority of web server
software including IIS and Apache based servers):
-----BEGIN CERTIFICATE-----
MIIE+jCCA+KgAwIBAgILAQAAAAABLc8cZm4wDQYJKoZIhvcNAQEFBQAwajEjMCEG
A1UECxMaT3JnYW5pemF0aW9uIFZhbGlkYXRpb24gQ0ExEzARBgNVBAoTCkdsb2Jh
bFNpZ24xLjAsBgNVBAMTJUdsb2JhbFNpZ24gT3JnYW5pemF0aW9uIFZhbGlkYXRp
b24gQ0EwHhcNMTEwMTI4MjM1NDA5WhcNMTIwMzEzMjEwNjExWjByMQswCQYDVQQG
EwJDQTEQMA4GA1UECBMHT250YXJpbzERMA8GA1UEBxMIV2F0ZXJsb28xHzAdBgNV
BAoTFlVuaXZlcnNpdHkgb2YgV2F0ZXJsb28xHTAbBgNVBAMMFHBsZzEuY3MudXdh
dGVybG9vLmNhMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAxYOQUZ4X
RfVa9YntRylvv7hf57itkG/se5fr1CfMiZZP7SWm7L+ZEl6PngLAvlVLyNe8bFL6
x6NjTCHAOxkTleCxr0bDPXrxjKb5ekA+4Y8TEy8XZzuKXNTe3C1GsC7KEdDWTW55
tJYn8ubIyyfMtF0DidSrujmSg+BeRBwMdL7HLtM9ZSo9HtX6LgI0UhEUJtFHJ9VJ
n4TC/rfX64tiDS1kpTUacxvkALXzsAbI6xeXo2zRiqCbkv4mK9U6Zc0tTE5UP4EE
nlRFYDfjVEskeoRl8zuulb4a9IVVuOLwdXEM71JshblVjebgWqf286P262VaoVTx
ZRtWHKpPLDUrEQIDAQABo4IBlzCCAZMwHwYDVR0jBBgwFoAUfW0q7Garp1E2qwJp
8XCPxFkLmh8wSQYIKwYBBQUHAQEEPTA7MDkGCCsGAQUFBzAChi1odHRwOi8vc2Vj
dXJlLmdsb2JhbHNpZ24ubmV0L2NhY2VydC9vcmd2MS5jcnQwPwYDVR0fBDgwNjA0
oDKgMIYuaHR0cDovL2NybC5nbG9iYWxzaWduLm5ldC9Pcmdhbml6YXRpb25WYWwx
LmNybDAdBgNVHQ4EFgQUnQS7i3B8caVD1vafco553LbJSKkwCQYDVR0TBAIwADAO
BgNVHQ8BAf8EBAMCBaAwKQYDVR0lBCIwIAYIKwYBBQUHAwEGCCsGAQUFBwMCBgor
BgEEAYI3CgMDMEsGA1UdIAREMEIwQAYJKwYBBAGgMgEUMDMwMQYIKwYBBQUHAgEW
JWh0dHA6Ly93d3cuZ2xvYmFsc2lnbi5uZXQvcmVwb3NpdG9yeS8wEQYJYIZIAYb4
QgEBBAQDAgbAMB8GA1UdEQQYMBaCFHBsZzEuY3MudXdhdGVybG9vLmNhMA0GCSqG
SIb3DQEBBQUAA4IBAQBGe926vpyQEs9Sk7d0sW2c8+FAL+cFn6JCayc1ua1v4WAh
wOpjHybXfmKik+adZtDKmAPEjAdD7MelElKxf79vYeILU8FkCy0u+N1HrfZEn2Dn
OFWThyFw5+fhRfmejg5QMFWkaEKpEE9MRQYBpYlfKnNBhGLbXWJk2lsRXqj6FgSk
KsLCOkyYpibyboWPJs1Js7C2pe14tcxx1SHPsTsGRveyqhp0S4E5VxQ2OVJX9vtm
Z6Z57cmZyGBa7N3NJ3mJZ44CCUTe4tVi69DU83vZ2oK2oL8pIp9UwKG5Obf9axfc
+hzesAhKSb27EG7YfAknG1dZUtkZvvj7XVP6bzHk
-----END CERTIFICATE-----
OrganizationSSL Intermediate Root Certificate (Formatted for the
majority of web server software including IIS and Apache based
servers):
-----BEGIN CERTIFICATE-----
MIIEZzCCA0+gAwIBAgILBAAAAAABHkSl9SowDQYJKoZIhvcNAQEFBQAwVzELMAkG
A1UEBhMCQkUxGTAXBgNVBAoTEEdsb2JhbFNpZ24gbnYtc2ExEDAOBgNVBAsTB1Jv
b3QgQ0ExGzAZBgNVBAMTEkdsb2JhbFNpZ24gUm9vdCBDQTAeFw0wNzA0MTExMjAw
MDBaFw0xNzA0MTExMjAwMDBaMGoxIzAhBgNVBAsTGk9yZ2FuaXphdGlvbiBWYWxp
ZGF0aW9uIENBMRMwEQYDVQQKEwpHbG9iYWxTaWduMS4wLAYDVQQDEyVHbG9iYWxT
aWduIE9yZ2FuaXphdGlvbiBWYWxpZGF0aW9uIENBMIIBIjANBgkqhkiG9w0BAQEF
AAOCAQ8AMIIBCgKCAQEAoS/EvM6HA+lnwYnI5ZP8fbStnvZjTmronCxziaIB9I8h
+P0lnVgWbYb27klXdX516iIRfj37x0JB3PzFDJFVgHvrZDMdm/nKOOmrxiVDUSVA
9OR+GFVqqY8QOkAe1leD738vNC8t0vZTwhkNt+3JgfVGLLQjQl6dEwN17Opq/Fd8
yTaXO5jcExPs7EH6XTTquZPnEBZlzJyS/fXFnT5KuQn85F8eaV9N9FZyRLEdIwPI
NvZliMi/ORZFjh4mbFEWxSoAOMWkE2mVfasBO6jEFLSA2qwaRCDV/qkGexQnr+Aw
Id2Q9KnVIxkuHgPmwd+VKeTBlEPdPpCqy0vJvorTOQIDAQABo4IBHzCCARswDgYD
VR0PAQH/BAQDAgEGMBIGA1UdEwEB/wQIMAYBAf8CAQAwHQYDVR0OBBYEFH1tKuxm
q6dRNqsCafFwj8RZC5ofMEsGA1UdIAREMEIwQAYJKwYBBAGgMgEUMDMwMQYIKwYB
BQUHAgEWJWh0dHA6Ly93d3cuZ2xvYmFsc2lnbi5uZXQvcmVwb3NpdG9yeS8wMwYD
VR0fBCwwKjAooCagJIYiaHR0cDovL2NybC5nbG9iYWxzaWduLm5ldC9yb290LmNy
bDARBglghkgBhvhCAQEEBAMCAgQwIAYDVR0lBBkwFwYKKwYBBAGCNwoDAwYJYIZI
AYb4QgQBMB8GA1UdIwQYMBaAFGB7ZhpFDZfKiVAvfQTNNKj//P1LMA0GCSqGSIb3
DQEBBQUAA4IBAQB5R/wV10x53w96ns7UfEtjyYm1ez+ZEuicjJpJL+BOlUrtx7y+
8aLbjpMdunFUqkvZiSIkh8UEqKyCUqBS+LjhT6EnZmMhSjnnx8VOX7LWHRNtMOnO
16IcvCkKczxbI0n+1v/KsE/18meYwEcR+LdIppAJ1kK+6rG5U0LDnCDJ+6FbtVZt
h4HIYKzEuXInCo4eqLEuzTKieFewnPiVu0OOjDGGblMNxhIFukFuqDUwCRgdAmH/
/e413mrDO9BNS05QslY2DERd2hplKuaYVqljMy4E567o9I63stp9wMjirqYoL+PJ
c738B0E0t6pu7qfb0ZM87ZDsMpKI2cgjbHQh
-----END CERTIFICATE-----
-----------------------------------------------------------------------------
GlobalSign - over 10 years of securing identities, web sites and transactions
-----------------------------------------------------------------------------
Generally speaking, the Intermediate Certificate will already
be installed on systems where you are renewing certificates.
If you are setting up a new SSL service for the first time,
you will need to ensure the Intermediate Certificate is appropriately
available.
Actually, I am rethinking that assumption right now. -- AdrianPepper - 29 Sep 2011
Installing and Testing
Installing the Certificate
Theoretically, the file system locations of old versions
of certificates could be almost arbitrary.
To be sure of updating (or installing anew) all certificates,
including the intermediate certificate, and private keys,
you would need to read the configuration for all server
applications involved, and install or replace the contents
in the appropriate format.
In practice, locations of certificates are constrained somewhat.
There are potentially four pieces of data to install or make accessible for each server application.
1. The host private key
2. The host certificate
3. The
OrganizationSSL (or
IntranetSSL) Intermediate Root Certificate
4. An appropriate
Certificate Authority Root Certificate
Of those,
2 (the host certificate) is the one you will always need to install or update.
If you generated a new
1 private key, you will need to ensure it is correctly updated
to match each certificate you install or update. In general
3 (intermediate certificate) will have been appropriately installed, unless you are
setting up a brand-new server.
And
4 (CA root certificate) isn't actually required by most server
applications.
A CA root certificate is really only meaningful to the clients
if it is obtained from a source different from the server presenting
a certificate allegedly signed by that authority.
Nonetheless, many servers are set up with CA root certificates available,
although most client and server software will not actually have any reason
to access that particular certificate from that source.
Certificate Location under Xhier
The great Xhier guru
Patrick Matlock
conceived that all applications configured
under xhier should have a single location in which SSL certificates
(and private keys) should be kept.
Therefore he created an sslCerts xhier package (which has had an
only version sslCerts-1) under which certificates should be stored.
On xhiered systems, certificates should be placed in
/software/sslCerts/config/certs/
and software configured to reference them from there.
Similarly private keys should be put in
/software/sslCerts/config/certs/private/
with configuration set appropriately.
Note that, although one suspects the idea was that directory should
be mode 700, it now tends to be 711 or worse, so you should make sure
the individual files are not readable by world or inappropriate groups.
(The search permission may be designed to allow daemons running as
non-root to access individual key files?)
An automated process, part of the sslCerts packages, makes sure
/software/sslCerts/config/certs/cacert.pem
contains the
OrganizationSSL certificate.
| Actually, I'm not certain IST updated the automated process when the intermediate certificate changed in 2011. |
In general, xhiered software which requires certificates will by
default refer to them in these locations.
Certificate Format Used by UW IMAPD and perhaps others
Here is the format of certificate files used by
stunnel
,
University of Washington
imapd
and
ipopd
and perhaps other servers.
Because the connections for these services are initiated by inetd,
startup efficiency is important
and so all necessary certificate information is placed in one file.
Because the private keys are included in these files, the
files must not be world-readable.
In addition it seems there can be no additional data before the first
-----BEGIN line
or
between the
-----END and
-----BEGIN lines--no readable certificate
forms or other comments. This is in contrast to other services which
do allow such comments.
root@services116.cs>2# cat stunnel.pem
-----BEGIN RSA PRIVATE KEY-----
MIICXAIBAAKBgQCeSOyOK6EZIqyG1cStXwsxlNlD/RayeMjjFBgn++9OjyRF/zUm
vnXUKBHi29z8yGgnWJ2cS8qYkAlfvhsmHAuOIQh3x/nuKtvCu1/ssghNXkMmVoJL
+Zkk2QaZX0bf8TnZ0OYC3qFS9HxgRKt6FIvsblbxme4mAreQMhpwDtB/+QIDAQAB
AoGAJHvmmraPwX1uiv3HAbdAm0MV+Ufi7WxN0ZmWH9FATblMwR2cILwR6L77sHDB
NTr0Vu1kFtyZbCT3JCxrkZMxTkqX/+uSh33+NNPc7gStwFQ7LjOyO6AthOpr4OIi
GzZrkVdlfvHakc9yoU3cBSNLbPuSefC6X773bM54KtZsDOkCQQDOGTqyXe3Uz3Oo
EaGpdvTZEi4+7X38HDydybFpl7aWu2ZEXgsRbwiWmM5j5mHmQBbBfWQv4+cDQLSN
i9IFkFt3AkEAxJwFRL+BBag039NCs8Ty8NirGrncsXHW2EnU1+ifZZBinp3Bg8G8
HTZKugG/W1ThLqNupvEfa4glzeQb+b78DwJAEdcbPp9k2/wNLepAzTOP5E5vlGDo
e+9Ry/LOma5ZTtjv9FETsjGjU63sh7dEmDLKBXu+NWsL7zslpe8JghPJ5wJACLDg
5r4UZPyfgblj/HBbUNwzDBZlNA7VMXBqETU+Po4YXeyZTkq1FxF8Uiabn9zrq1Uc
IhMMkYNOMIDB39NabwJBAKogdyM76Zfgd9I1fZf8AQKZVs4C1yq0JdPW6nl0gpKK
+nMCU7RIx0mdrEsTJNyR63hdPJ/37+OjvtRefBMVowE=
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIIEdjCCA16gAwIBAgILAQAAAAABJ24e8gcwDQYJKoZIhvcNAQEFBQAwajEjMCEG
A1UECxMaT3JnYW5pemF0aW9uIFZhbGlkYXRpb24gQ0ExEzARBgNVBAoTCkdsb2Jh
bFNpZ24xLjAsBgNVBAMTJUdsb2JhbFNpZ24gT3JnYW5pemF0aW9uIFZhbGlkYXRp
b24gQ0EwHhcNMTAwMzE3MjEyNDE3WhcNMTEwMzE4MjEyNDExWjByMQswCQYDVQQG
EwJDQTEQMA4GA1UECBMHT250YXJpbzERMA8GA1UEBxMIV2F0ZXJsb28xHzAdBgNV
BAoTFlVuaXZlcnNpdHkgb2YgV2F0ZXJsb28xHTAbBgNVBAMMFG1haWwuY3MudXdh
dGVybG9vLmNhMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDhrXXLjlNIBjkX
+FF9xV99R9dzOFNTuMvAZew18VOQzwscyVvxilVeXRjQoKB2osz22VNCof/Uf9pm
VSH5enWP5XwIUopkMG5uJGPOAPzr4smrEOVQ68VCtgR/M62iH9w6nuh1uUACgqW9
7ykzhwUZq5wntqBsnNvBszxHpUeZqwIDAQABo4IBlzCCAZMwHwYDVR0jBBgwFoAU
fW0q7Garp1E2qwJp8XCPxFkLmh8wSQYIKwYBBQUHAQEEPTA7MDkGCCsGAQUFBzAC
hi1odHRwOi8vc2VjdXJlLmdsb2JhbHNpZ24ubmV0L2NhY2VydC9vcmd2MS5jcnQw
PwYDVR0fBDgwNjA0oDKgMIYuaHR0cDovL2NybC5nbG9iYWxzaWduLm5ldC9Pcmdh
bml6YXRpb25WYWwxLmNybDAdBgNVHQ4EFgQUa4CiDe86Vx2LK1uGANpOHnoOtaEw
CQYDVR0TBAIwADAOBgNVHQ8BAf8EBAMCBaAwKQYDVR0lBCIwIAYIKwYBBQUHAwEG
CCsGAQUFBwMCBgorBgEEAYI3CgMDMEsGA1UdIAREMEIwQAYJKwYBBAGgMgEUMDMw
MQYIKwYBBQUHAgEWJWh0dHA6Ly93d3cuZ2xvYmFsc2lnbi5uZXQvcmVwb3NpdG9y
eS8wEQYJYIZIAYb4QgEBBAQDAgbAMB8GA1UdEQQYMBaCFG1haWwuY3MudXdhdGVy
bG9vLmNhMA0GCSqGSIb3DQEBBQUAA4IBAQAnAMxl6RKmiO6kBHkcrcNAdevfpC9h
UYN4u3XMYpsdkK03LtneRnVBVY5RBKw49WaEavJgFNXL/dGDJ1nAFSUqX/LnV6vR
wvrwArdruwNvMCOSHhTSzEI94TU8pYuqtG5JodTrVb9fGEXwmrQJp+Een974zWRE
HHQQ/NGjcBPTI+ts8BoTQaMZGEcxZ2zGHUTChbmVzjZgZPzIMSEcMGKuTAY1weGP
LyFKn7dOxIbN0lQVezCfHtSntTGaoLum5phnbsrU5qRTnVndDYSOtgS4wU2pXWal
ezqliW3+kStgu67NMOVtJP2yd3VNaDILoLme2OJiMNRTf27zyo6QAn1p
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIEZzCCA0+gAwIBAgILBAAAAAABHkSl9SowDQYJKoZIhvcNAQEFBQAwVzELMAkG
A1UEBhMCQkUxGTAXBgNVBAoTEEdsb2JhbFNpZ24gbnYtc2ExEDAOBgNVBAsTB1Jv
b3QgQ0ExGzAZBgNVBAMTEkdsb2JhbFNpZ24gUm9vdCBDQTAeFw0wNzA0MTExMjAw
MDBaFw0xNzA0MTExMjAwMDBaMGoxIzAhBgNVBAsTGk9yZ2FuaXphdGlvbiBWYWxp
ZGF0aW9uIENBMRMwEQYDVQQKEwpHbG9iYWxTaWduMS4wLAYDVQQDEyVHbG9iYWxT
aWduIE9yZ2FuaXphdGlvbiBWYWxpZGF0aW9uIENBMIIBIjANBgkqhkiG9w0BAQEF
AAOCAQ8AMIIBCgKCAQEAoS/EvM6HA+lnwYnI5ZP8fbStnvZjTmronCxziaIB9I8h
+P0lnVgWbYb27klXdX516iIRfj37x0JB3PzFDJFVgHvrZDMdm/nKOOmrxiVDUSVA
9OR+GFVqqY8QOkAe1leD738vNC8t0vZTwhkNt+3JgfVGLLQjQl6dEwN17Opq/Fd8
yTaXO5jcExPs7EH6XTTquZPnEBZlzJyS/fXFnT5KuQn85F8eaV9N9FZyRLEdIwPI
NvZliMi/ORZFjh4mbFEWxSoAOMWkE2mVfasBO6jEFLSA2qwaRCDV/qkGexQnr+Aw
Id2Q9KnVIxkuHgPmwd+VKeTBlEPdPpCqy0vJvorTOQIDAQABo4IBHzCCARswDgYD
VR0PAQH/BAQDAgEGMBIGA1UdEwEB/wQIMAYBAf8CAQAwHQYDVR0OBBYEFH1tKuxm
q6dRNqsCafFwj8RZC5ofMEsGA1UdIAREMEIwQAYJKwYBBAGgMgEUMDMwMQYIKwYB
BQUHAgEWJWh0dHA6Ly93d3cuZ2xvYmFsc2lnbi5uZXQvcmVwb3NpdG9yeS8wMwYD
VR0fBCwwKjAooCagJIYiaHR0cDovL2NybC5nbG9iYWxzaWduLm5ldC9yb290LmNy
bDARBglghkgBhvhCAQEEBAMCAgQwIAYDVR0lBBkwFwYKKwYBBAGCNwoDAwYJYIZI
AYb4QgQBMB8GA1UdIwQYMBaAFGB7ZhpFDZfKiVAvfQTNNKj//P1LMA0GCSqGSIb3
DQEBBQUAA4IBAQB5R/wV10x53w96ns7UfEtjyYm1ez+ZEuicjJpJL+BOlUrtx7y+
8aLbjpMdunFUqkvZiSIkh8UEqKyCUqBS+LjhT6EnZmMhSjnnx8VOX7LWHRNtMOnO
16IcvCkKczxbI0n+1v/KsE/18meYwEcR+LdIppAJ1kK+6rG5U0LDnCDJ+6FbtVZt
h4HIYKzEuXInCo4eqLEuzTKieFewnPiVu0OOjDGGblMNxhIFukFuqDUwCRgdAmH/
/e413mrDO9BNS05QslY2DERd2hplKuaYVqljMy4E567o9I63stp9wMjirqYoL+PJ
c738B0E0t6pu7qfb0ZM87ZDsMpKI2cgjbHQh
-----END CERTIFICATE-----
root@services116.cs>2#
Although I based this on an actual certificate chain, I substituted
an incorrect private key.
The contents are:
-----BEGIN RSA PRIVATE KEY-----
[ Private key for the host certificate immediately following ]
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
[ Host certificate (corresponds to that private key) ]
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
[ Intermediate OrganizationSSL Certificate..... ]
-----END CERTIFICATE-----
The
openssl command can be used, as in
openssl x509 -text, using one of the certificate
portions as input.
That will show a readable (well, verbose) form
of the certificate.
That can be useful to help be sure you are replacing the correct
host certificate, and also to check the expiry date, etc.
But remember that data such as that cannot be included in the installed
file; it will cause the service to stop working.
Note that no Certificate Authority Certificate is included.
That's because a Certificate Authority Certificate is really only meaningful if
the client obtains it from a source different from the server providing the
service. Note how the
OrganizationSSL Intermediate Root Certificate is used to connect the host certificate to the Certificate Authority.
Note that the private key and host certificate shown are only 1024-bit;
GlobalSign now requires 2048-bit keys, and so on renewal the above would
be (have been) upgraded.
Certificate Format Used by most Web and SMTP Servers
Here is the format of certificate files used for
web
,
SMTP
and perhaps other servers.
The private keys must not be world-readable, but the certificates
themselves can. Typically, the private keys are stored in not-world-readable
files in a subdirectory "private" which can also be not-world-readable.
root@services08.student.cs>2# pwd
/fsys1/.software/local/sslCerts-1/config/certs
root@services08.student.cs>2# cat private/httpsd-key.pem
-----BEGIN RSA PRIVATE KEY-----
MIIEpQIBAAKCAQEAzIFZVDKTDnooK5rCFVwKVDVpirsOxh5oqudSIUyxPH5pG7wJ
vGGBwdHgoyo/J9LZEieBWcqlLXXMK7IALAmo3MKJ8V8A3G65DrD2nc0PbZFWlu8D
WadeM53hKBcAcSilFR+IjAiAPK5w0xm5jfFL48nfnWDHdwcc2wILYnQLgwDORLH4
1fkGYGtGfGKA8QLtFpR1SJOFnNFwq4GAb1ibIHEitIfAQG3LEpn0bUKACDuKAJVI
/yI+AUlBS92r/YPzE0Hs07DwcqB0cqQk1E0AIkaWyTzSHFnvI0Izv+HBOFhbIquD
MbNlE8u8QxF7Gdt8St5DKm3VXmFnzYsk5Bj9aQIDAQABAoIBAQCfQWurIedbMs3t
hwr1T0PL5/xUyO7sYenojVNsEylCjr6Tlo+OX/CIW0SwS8n63Tul45Xbsu+Gw2FH
9cokgTE7GVQK34zwHFmIk065/GKzVKc1ytO1EZ1OXPhmG+OAO8Ky/Gd9hXE30DCU
dEgHvYz3ytGU4TT0AFn8Q09SUERWsvkztQQI3R/yMdekaGQf3LP8whKj+IRKBJgN
LfJelGCuaq5UfyiRX15tu4YpES6cZ0gB0ZT3/FhbS3tfPFX7rb6FyDowxBS5cRTk
usCqURDy4U6/Zb4QASUc1vNxzJhIc0kMHwNAYbrwgIkIz3dPh8MyzYilZAkA4rLz
XJY8Wk4BAoGBAO9aH0cCl8xjJscnUcHXGJDW8m3MznzAWZ03NZ3jAHyxLrYuAF+6
SsubS65tmMoNf15slB4oOb6m2WtctqqOMa1xxkTEzKwOHpv3sSWGi/DpvggwgahN
l+HxBS6eX4kRDQr6Zqj8EbjNdLQWhsfsL6nPKriOym9Dbi4qbZlBx9TxAoGBANq6
v64VlggXyJdgyGRejRo1sNb1M+2zl7zkpXRAlnt6ie3iS5mqEndIyXf0q8dyjKLL
ZN9uGx4vDwhDBcDEhAASAn0OMrYCSJcumz/OE5Zk4ltEx52rh3VR4R/QBwjL7HY4
4cITQas4YLw+egvEZguIeoWEXD0rZ3+XR6HcTM/5AoGBAKbv13LCdzdBTFGItfgZ
WnPixxEX0EioK5iAYi/tnHBbb7X2naImn3YkqQNOQ0thYJ1t41ypN6UmX+wGrQyF
wlYzTVK3Y/z4mBa2CeKfVclAbZ7une/RtoYKgU/De+RwdQVcIe/oZz/aZHQaZgTY
UWIBMM2qIby6bgVa6DgE7igxAoGBAK+3QQ+wJbRgrvP1e2cukjqREXzOxaXbFjZY
lRa8YGfYPIBPwJ41A9qyLa/hbjKvMo4Bygq4oK5x7aicdz2yYbzQuxEN2+1eDkTt
2yi5/ABhEXty2M4wo4S7f5iX/V6yvEcJUUwhPis4AnaX1mInqDbxsEQc3iECAoZ8
2L4OheK5AoGAdJLuCK/VqB+bjqdSuv+id4UhVyB4cPqkNyHt3Yqydi+KYYj2iIAe
Kel0739XTJXv4GaL6T4Cl5ZZHxajTzrbV36XthSOfIBE3IAdeEcwWoQF4ISwEyLP
vrnRcgUQEWUbSxSGU+OZDqa80E6Uqe4lPLnXC2BMxdGWNTV1AN4gsF8=
-----END RSA PRIVATE KEY-----
root@services08.student.cs>2#
root@services08.student.cs>2# cat httpsd.pem
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
01:00:00:00:00:01:27:e4:b2:1c:14
Signature Algorithm: sha1WithRSAEncryption
Issuer: OU=Organization Validation CA, O=GlobalSign, CN=GlobalSign Organization Validation CA
Validity
Not Before: Apr 9 21:30:10 2010 GMT
Not After : May 20 13:14:24 2011 GMT
Subject: C=CA, ST=Ontario, L=Waterloo, O=University of Waterloo, CN=www.student.cs.uwaterloo.ca
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Modulus (1024 bit):
00:b2:35:32:33:ed:6c:f4:6d:b5:5c:39:55:b7:2f:
1c:ca:b4:8f:0e:5f:58:dc:4e:c5:8f:50:a0:83:04:
bd:48:ac:48:49:ed:a1:6d:4d:d6:ef:86:2a:0c:2a:
c3:87:57:c0:37:9b:20:03:72:f1:a0:4f:2a:7d:4b:
b4:51:e1:13:03:37:14:f5:49:91:25:21:ca:e0:a6:
e2:71:e4:23:d2:ff:51:ff:d1:a4:b4:f2:9b:7d:4e:
cd:49:4f:73:a3:34:5e:a0:f0:7d:ad:11:11:3b:46:
1d:cb:c5:d2:95:69:50:18:0c:f4:1b:d3:d9:af:7f:
1c:f4:77:de:c0:20:28:0d:71
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Authority Key Identifier:
keyid:7D:6D:2A:EC:66:AB:A7:51:36:AB:02:69:F1:70:8F:C4:59:0B:9A:1F
Authority Information Access:
CA Issuers - URI:http://secure.globalsign.net/cacert/orgv1.crt
X509v3 CRL Distribution Points:
URI:http://crl.globalsign.net/OrganizationVal1.crl
X509v3 Subject Key Identifier:
DC:55:92:06:B7:F7:0A:D5:4C:78:C3:AA:1D:9E:71:FA:BA:2D:90:04
X509v3 Basic Constraints:
CA:FALSE
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication, Microsoft Server Gated Crypto
X509v3 Certificate Policies:
Policy: 1.3.6.1.4.1.4146.1.20
CPS: http://www.globalsign.net/repository/
Netscape Cert Type:
SSL Client, SSL Server
X509v3 Subject Alternative Name:
DNS:www.student.cs.uwaterloo.ca, DNS:student.cs.uwaterloo.ca
Signature Algorithm: sha1WithRSAEncryption
3f:04:fd:0d:9f:dc:e1:9e:c3:df:25:c6:a4:7b:d3:80:4a:11:
85:d7:c2:5a:be:46:92:25:62:f1:ae:c0:88:53:cb:02:dd:10:
07:05:e9:dc:ef:c3:7b:fd:67:44:ec:c1:f6:45:e8:d6:be:26:
56:51:94:41:4c:c7:51:45:4d:52:5e:a8:e2:08:82:b7:58:5f:
44:f8:1c:21:c4:6c:c7:37:d4:2f:a3:9e:f2:80:c9:14:b2:8f:
77:f5:6e:81:0b:27:b3:08:14:43:2e:5b:e0:1f:9b:02:60:36:
07:e6:8f:c9:cf:34:40:19:67:de:93:a3:fe:3c:b4:17:66:4f:
7e:e9:c5:f3:8f:91:9c:18:7f:3b:b1:c7:8f:7a:a6:ba:e1:30:
51:4b:6c:ca:33:7e:d6:91:0e:69:27:46:a4:08:2e:a7:7d:d5:
06:82:ca:3c:e2:48:1d:48:5d:1a:35:42:48:53:50:60:40:6b:
b6:b0:00:39:0d:af:b5:45:9d:ca:2d:0b:61:be:b8:c0:2e:05:
7d:9a:43:c8:b2:d5:81:a0:10:12:fd:21:a2:39:6a:5f:8b:90:
70:5c:60:e0:ef:ad:d4:c6:6c:1b:70:36:9c:2c:2b:88:79:a5:
82:dc:a3:37:6c:94:2d:f7:c2:1f:be:b1:37:60:47:08:6a:70:
50:81:fa:52
-----BEGIN CERTIFICATE-----
MIIEnTCCA4WgAwIBAgILAQAAAAABJ+SyHBQwDQYJKoZIhvcNAQEFBQAwajEjMCEG
A1UECxMaT3JnYW5pemF0aW9uIFZhbGlkYXRpb24gQ0ExEzARBgNVBAoTCkdsb2Jh
bFNpZ24xLjAsBgNVBAMTJUdsb2JhbFNpZ24gT3JnYW5pemF0aW9uIFZhbGlkYXRp
b24gQ0EwHhcNMTAwNDA5MjEzMDEwWhcNMTEwNTIwMTMxNDI0WjB5MQswCQYDVQQG
EwJDQTEQMA4GA1UECBMHT250YXJpbzERMA8GA1UEBxMIV2F0ZXJsb28xHzAdBgNV
BAoTFlVuaXZlcnNpdHkgb2YgV2F0ZXJsb28xJDAiBgNVBAMMG3d3dy5zdHVkZW50
LmNzLnV3YXRlcmxvby5jYTCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEAsjUy
M+1s9G21XDlVty8cyrSPDl9Y3E7Fj1CggwS9SKxISe2hbU3W74YqDCrDh1fAN5sg
A3LxoE8qfUu0UeETAzcU9UmRJSHK4KbiceQj0v9R/9GktPKbfU7NSU9zozReoPB9
rRERO0Ydy8XSlWlQGAz0G9PZr38c9HfewCAoDXECAwEAAaOCAbcwggGzMB8GA1Ud
IwQYMBaAFH1tKuxmq6dRNqsCafFwj8RZC5ofMEkGCCsGAQUFBwEBBD0wOzA5Bggr
BgEFBQcwAoYtaHR0cDovL3NlY3VyZS5nbG9iYWxzaWduLm5ldC9jYWNlcnQvb3Jn
djEuY3J0MD8GA1UdHwQ4MDYwNKAyoDCGLmh0dHA6Ly9jcmwuZ2xvYmFsc2lnbi5u
ZXQvT3JnYW5pemF0aW9uVmFsMS5jcmwwHQYDVR0OBBYEFNxVkga39wrVTHjDqh2e
cfq6LZAEMAkGA1UdEwQCMAAwDgYDVR0PAQH/BAQDAgWgMCkGA1UdJQQiMCAGCCsG
AQUFBwMBBggrBgEFBQcDAgYKKwYBBAGCNwoDAzBLBgNVHSAERDBCMEAGCSsGAQQB
oDIBFDAzMDEGCCsGAQUFBwIBFiVodHRwOi8vd3d3Lmdsb2JhbHNpZ24ubmV0L3Jl
cG9zaXRvcnkvMBEGCWCGSAGG+EIBAQQEAwIGwDA/BgNVHREEODA2ght3d3cuc3R1
ZGVudC5jcy51d2F0ZXJsb28uY2GCF3N0dWRlbnQuY3MudXdhdGVybG9vLmNhMA0G
CSqGSIb3DQEBBQUAA4IBAQA/BP0Nn9zhnsPfJcake9OAShGF18JavkaSJWLxrsCI
U8sC3RAHBenc78N7/WdE7MH2RejWviZWUZRBTMdRRU1SXqjiCIK3WF9E+BwhxGzH
N9Qvo57ygMkUso939W6BCyezCBRDLlvgH5sCYDYH5o/JzzRAGWfek6P+PLQXZk9+
6cXzj5GcGH87scePeqa64TBRS2zKM37WkQ5pJ0akCC6nfdUGgso84kgdSF0aNUJI
U1BgQGu2sAA5Da+1RZ3KLQthvrjALgV9mkPIstWBoBAS/SGiOWpfi5BwXGDg763U
xmwbcDacLCuIeaWC3KM3bJQt98IfvrE3YEcIanBQgfpS
-----END CERTIFICATE-----
root@services08.student.cs>2#
Although I based this on actual certificates, I substituted
an incorrect private key.
The
openssl command can be used, as in
openssl x509 -text, using one of the certificate
portions as input.
That will show a readable (well, verbose) form
of the certificate.
That can be useful to help be sure you are replacing the correct
host certificate, and also to check the expiry date, etc.
Typically, as is shown here, the previous installer will include that
information in the .pem file. But it is optional, and occasionally
the text may not match the certificate.
The following matches a particular sequence known to exist in the
encoding of the
OrganizationSSL certificate, in order to find and
extract it from the
cacert.pem file where the Apache web software
is typically configured to find it.
perl -ane < /software/sslCerts/config/certs/cacert.pem \
'if(/---BEGIN C/){$c="";$p=0}; \
if(/^c738B0E0t6pu7qfb0/){$p=1}; \
$c.=$_;if(/---END C/){if($p){print $c;$p=0}}'
To see details of that certificate, you could even do...
perl -ane < /software/sslCerts/config/certs/cacert.pem \
'if(/---BEGIN C/){$c="";$p=0}; \
if(/^c738B0E0t6pu7qfb0/){$p=1}; \
$c.=$_;if(/---END C/){if($p){print $c;$p=0}}' | openssl x509 -text
Relevant Apache config lines will look like...
root@services08.student.cs>2# pwd
/fsys1/.software/local/wwwapache-1.3_server/config
root@services08.student.cs>2# grep /sslC * /dev/null /dev/null | grep -v ':#'
httpd.conf: SSLCertificateFile /software/sslCerts-1/config/certs/odyssey.student.cs.uwaterloo.ca.pem
httpd.conf: SSLCertificateKeyFile /software/sslCerts-1/config/certs/private/httpsd-key.pem
httpd.conf:SSLCACertificateFile /software/sslCerts-1/config/certs/cacert.pem
root@services08.student.cs>2#
Which reveals a lie in our presentation. The
www.student.cs.uwaterloo.ca certificate has actually been superseded
by the
odyssey.student.cs.uwaterloo.ca certificate. (Note that
correspondence between names of files and the certificates they contain
is not mandatory, but is advisable).
It is beyond the scope of these pages to tell you how to set up such
Apache configuration; what is here is just hints to help you analyze
any particular configuration for which you may have been entrusted with
the update of a certificate.
Anecdotal warning: although Apache will find the OrganizationSSL certificate from the cacert.pem file, as it is configured to do in the example, that OrganizationSSL certificate can in fact be placed in the SSLCertificateFile. In such a case the SSLCACertificateFile may in fact not be defined. At least once it happened that such a pair of certificates was replaced during renewal by the host certificate only. With no SSLCACertificateFile defined, the web server could not return the OrganizationSSL certificate. However, that was initially undetected because clients (web browsers) typically will be able to use the certificate they obtained from another uwaterloo.ca web site. That is, the problem thus created is only evident if the thusly broken site is the first uwaterloo.ca site a browser visits.
Further experimentation suggests that the previous was true only for Apache 1.3, if at all. Apache 2 appears to require the variable SSLCertificateChainFile to be specified if you wish to include a chain of several certificates. |
Testing
Using openssl command to check Certificate installations
The
openssl command has an
s_client sub-command which can
be a simple client for SSL smtp, imap, pop or ftp.
arpepper@cscfpc20:~$ echo quit | openssl s_client -crlf -connect mail.cs.uwaterloo.ca:465
arpepper@cscfpc20:~$ echo quit | openssl s_client -starttls smtp -crlf -connect mail.cs.uwaterloo.ca:25
arpepper@cscfpc20:~$ echo 0 logout | openssl s_client -starttls imap -crlf -connect mail.cs.uwaterloo.ca:imap
arpepper@cscfpc20:~$ echo 0 logout | openssl s_client -crlf -connect mail.cs.uwaterloo.ca:imaps
arpepper@cscfpc20:~$ echo quit | openssl s_client -starttls pop3 -crlf -connect plg2.cs.uwaterloo.ca:110
arpepper@cscfpc20:~$ echo quit | openssl s_client -crlf -connect plg2.cs.uwaterloo.ca:995
I had to hunt around for a
pop3 example, because that is being shut down.
The output from the above is lengthy, and includes the main server
certificate.
You can use the
openssl command to view its details.
Other options can be given to the above. Most useful might be
-showcerts
which will show the entire certificate chain. Also
-CAfile <file> or
-CApath <dir>.
arpepper@cscfpc20:~$ echo 0 logout | openssl s_client -showcerts -CApath /etc/ssl/certs -starttls imap -crlf -connect mail.cs.uwaterloo.ca:imap
-starttls http is not supported, since there is no such concept. But since
https is a standard
SSL protocol port, the following does work to view the certificate used by https:
arpepper@cscfpc20:~$ cat /dev/null | openssl s_client -crlf -connect cs.uwaterloo.ca:443
Since
openssl x509 -text does ignore information outside the recognized
CERTIFICATE area, the above commands can all be piped directly into it.
arpepper@cscfpc20:~$ echo 0 logout | openssl s_client -starttls imap -crlf -connect mail.cs.uwaterloo.ca:imap | openssl x509 -text
There might be a little untidy
stderr output at the beginning, so...
arpepper@cscfpc20:~$ echo 0 logout | 2>/dev/null openssl s_client -starttls imap -crlf -connect mail.cs.uwaterloo.ca:imap | openssl x509 -text
Testing a Recently Changed Web Server Certificate
It is easy to check what certificate is being presented using
the
FireFox browser.
However, you should verify that the
OrganizationSSL Intermediate Root Certificate
has been installed correctly.
FireFox will show you the chain of certificates, but a problem
is it might have remembered the intermediate certificate from another
University of Waterloo site.
You can ensure
FireFox gets the certificate from your web server
by creating a new, empty profile using
arpepper@cscfpc20:~$ firefox -no-remote -ProfileManager
Choose "Create Profile" and then complete the one-step wizard
to create a new empty profile (you just need to choose a name),
and then click on that profile to start a session using it.
And then immediately browse to an https page on the server
whose certificate you have just updated.
There should be no negative diagnostics, although the default
warning about an encrypted page should occur.
With version of
FireFox available as I write this page, choose
[Tools] => [Page Info]
[Security] => [View Certificate]
The Expiry Date is visible (although the date format is obscure).
[Details]
should show you the Intermediate Certificate as
GlobalSign Organization Validation CA - G2; you should be able to
confirm the validity dates. (Although it's a little painful).
(Older certificates will have been using simply
GlobalSign Organization Validation CA).
Although this facility should remain available in future
FireFox, details of the interface will probably change.
For tidiness, you probably want to immediately delete your new
profile using the dialog generated by:
arpepper@cscfpc20:~$ firefox -no-remote -ProfileManager
and then selecting it for [Delete].
(You will want a brand new profile for any future tests; this
one will have become "contaminated").
| If the certificate chain was not set up correctly, you will probably have difficulty even navigating to the page in question--You will get errors complaining about an untrusted certificate authority. |
--
AdrianPepper - 01 Jun 2012
There is a website that verifies certificates:
http://www.digicert.com/help/
It seems to go beyond what even
FireFox wants - if the certificate chain is out of order it will display the links in red, even though all the appropriate certificates are present.
--
IsaacMorland
Get Certificates from a Web Page using Firefox
If you are viewing an https page in
FireFox then you can perform the
following menu/button selections to save its certificates.
[Tools]
. => [Page Info]
... => [Security]
..... => [View Certificate]
........ => [Details]
........... => [Export]
You can choose to save the certificate and/or chain as PEM, DER, or PKCS#7.
The files you save can then be manipulated using the appropriate
openssl commands.
This was the case with the
FireFox version I had available at the time of
writing. YMMV.
Testing a Recently Changed Mail Server Certificate
It is not easy to check what certificate is being presented using
the
ThunderBird mail client.
However, you should verify that both host certificate and the
OrganizationSSL Intermediate Root Certificate
have been installed correctly.
ThunderBird will show you the chain of certificates.
You can ensure
ThunderBird gets the certificates from the mail server
by creating a new, empty profile using
arpepper@cscfpc20:~$ thunderbird -no-remote -ProfileManager
Choose "Create Profile" and then complete the one-step wizard to
create a new empty profile (you just need to choose a name).
Then click on that profile to start a session using it.
You will be asked to set up an account.
When asked for imap and smtp server, enter a version of the name
which will not actually match the full name in the certificate
you wish to test.
For example, enter just
plg.cs
instead of
plg.cs.uwaterloo.ca.
If the host uses
imaps and not
TLS under
imap the profile
will fail initially, and you will need to find and click
[View settings for this account] and [Server Settings] and change
the connection type to
SSL.
If you then click on
Inbox,
you should get a warning about the name mismatch, in a dialog
box which allows you to [View Certificate].
[Details]
should show you the Intermediate Certificate as
GlobalSign Organization Validation CA; you should be able to
confirm its validity dates (Although the procedure is a little painful).
There does not appear to be any way to save or export any of the
certificates.
Although this facility should remain available in future
ThunderBird, details of the interface will probably change.
For tidiness, you probably want to immediately delete your new
profile using the dialog generated by:
arpepper@cscfpc20:~$ thunderbird -no-remote -ProfileManager
and then selecting it for [Delete].
--
AdrianPepper - 2015-04-07
--
AdrianPepper - 2021-10-20
 There is an option you must select to choose new certificate or
renewal.
If
There is an option you must select to choose new certificate or
renewal.
If 