Remote Authentication Dial-in User Service (RADIUS) is a system that uses a central server running RADIUS software to control access to RADIUS-aware switches on the network. A RADIUS server can be used to create a database of mulitple user name/password pairs with associated privilege levels for each user or group that require management access to a switch using the console port, Telnet or web.
When setting up privilege levels on the RADIUS server, command access to the switch can be set at level 1 for Normal Exec mode or level 15 for Privileged Exec mode.
The RADIUS Settings page contains the following editable fields:
| NOTE: The local switch user database has to be set up by manually entering user names and passwords using the CLI. |
To save any changes you make in this page, click Apply Changes. To reset these fields to their current value, click Refresh.
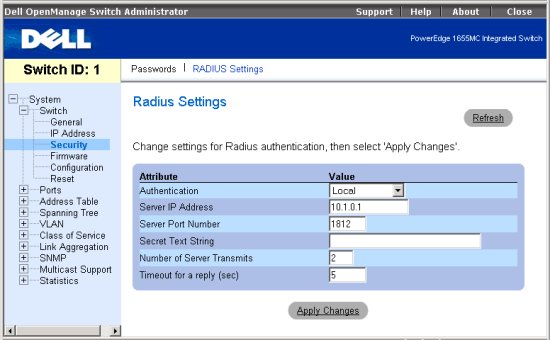
The following is a summary of the equivalent CLI commands for items in the Switch/Security/RADIUS Settings web page.
| Command | Usage |
| authentication login {radius | local | radius local | local radius} | Use this command to define the login authentication method and precedence. |
| radius server host host_ip_address | Use this command to specify the RADIUS server IP address. |
| radius server port port_number | Use this command to set the RADIUS server UDP port number. |
| radius server key key_string | Use this command to set the RADIUS encryption key. |
| radius server retransmit number_of_retries | Use this command to set the number of times the switch will try to authenticate logon access via the RADIUS server. (Range is 1 - 30.) |
| radius server timeout number_of_seconds | Use this command to set the number of seconds the switch waits for a reply before resending a request. |
Example
|
Console(config)# authentication
login radius |